To access material, start machines and answer questions login.
Understanding Advanced Persistent Threats, or APTs, is essential for anyone working in cyber security, as they represent some of the most sophisticated and stealthy attacks in the cyber world. This room focuses specifically on APT28, one of the most well-known and active threat groups. You’ll explore how APT28 operates, their objectives, and the techniques they use to gain access, maintain persistence, escalate privileges, lateral movement, and exfiltrate data.
It’s worth noting that this is a theoretical room that describes the behavior of the Fancy Bear group. Independent research is required to find answers to some of the room's questions, as it helps gain deeper insight into incidents associated with this group.
This room is primarily designed for SOC L2/L3 analysts, DFIR team members, Threat Hunters, and Security Researchers who want to get familiar with APT28.
Learning Objectives
- Understand the history, motivations, and targeted sectors of APT28.
- Examine APT28's operations and major attack campaigns.
- Explain the initial access techniques used by APT28, such as phishing, zero-day exploits, and other vulnerabilities.
- Explore APT28’s persistence and privilege escalation techniques.
- Examine lateral movement and data exfiltration methods used by APT28.
Room Prerequisites
It is suggested to clear the following rooms first before proceeding:
Ready to enhance your knowledge about threat groups? Let’s get started!
Let's go!
What are Advanced Persistent Threats (APTs)?
An Advanced Persistent Threat refers to a group of individuals that collaborate over an extended period to gain access and maintain an unauthorised presence to specific targets. These groups typically aim to steal sensitive data, engage in cyber espionage, or disrupt critical systems. APTs are often state-sponsored or associated with organised groups, utilising various deceptive tactics to go undetected while they gather intelligence and compromise their targets. Unlike conventional cybercriminals who might pursue immediate financial gain, APT actors focus on long-term infiltration and stealthy operations. These groups usually start with thorough reconnaissance to identify vulnerabilities in their target's defences. They may employ social engineering techniques and custom malware to exploit specific weaknesses. Once they gain access, they work to expand their presence within the network, enabling them to extract valuable information over time. The primary objective of an APT is to achieve persistent access to a target, which can have serious implications for organisations and governments.
How do APTs Work?
An Advanced Persistent Threat attack progresses in several stages, allowing attackers to gain initial point, maintain access, and extract sensitive information while remaining undetected:
- Intelligence Gathering: Attackers perform reconnaissance to identify targets and vulnerabilities, carefully planning their strategy to avoid detection.
- Entry Points & Infiltration: They gain access through methods like phishing or exploiting vulnerabilities. Once inside, they establish persistence mechanisms for ongoing access.
- Command & Control: After establishing a foothold, attackers communicate with external servers to manage their next steps.
- Lateral Movement: Hackers navigate the network to identify valuable assets, often targeting privileged staff. They masquerade as legitimate traffic to evade detection.
- Exfiltration: After gathering data, attackers exfiltrate sensitive information while using distractions, such as DDoS attacks, to evade detection.
Goals of APT Groups
Advanced Persistent Threat groups have specific, often strategic objectives, that drive their operations. Understanding these goals can help organisations better prepare and defend against such threats. Here's what APT groups typically aim for:
- Data Theft: One of the primary motivations for APT groups is to steal sensitive information. This could be anything from trade secrets and intellectual property to confidential government documents. By gaining access to valuable data, they can give their nation or organisation a significant advantage over competitors.
- Espionage: Many APT groups are linked to state-sponsored activities, focusing on cyber espionage to gather intelligence on other countries or organisations. For example, the Cozy Bear group, believed to be affiliated with the Russian government, was involved in the hack of the U.S. Democratic National Committee in 2016. This operation aimed to gather sensitive information and influence the U.S. electoral process.
- Disruption: APT groups may also aim to disrupt critical infrastructure. By targeting essential services like energy or transportation, they can create chaos and instability. For instance, an attack on power grids can lead to widespread outages, affecting entire regions. An example of this is the Shamoon malware attack that targeted Saudi Aramco in 2012. The attackers wiped data from thousands of computers, crippling operations and causing significant disruptions in oil production and distribution.
- Long-Term Access: Unlike many cybercriminals who pursue quick financial gain, APT groups aim for sustained access to their targets. They establish a foothold in the network, allowing them to gather intelligence continuously, launch future attacks, or exploit vulnerabilities over time.
Recognising these goals is crucial for organisations to strengthen their defences and respond effectively to potential APT threats. By being aware of what motivates these attackers, businesses can take proactive steps to safeguard their sensitive information and maintain operational integrity.
In this room, we will focus specifically on APT28, exploring their tactics, techniques, and notable activities. However, before we transition to our discussion on APT28, you'll need to answer a few questions. This may require some OSINT, but it will be an engaging experience!
APT28 Overview
APT28, also known as Fancy Bear or Sofacy, is a prominent Russian cyber espionage group linked to the military intelligence agency the GRU. Active since at least 2004, this group focuses on gathering intelligence and executing cyber operations that align with the Russian government's strategic interests. Their specific military unit, GRU Unit 26165, is tasked with carrying out these operations. Fancy Bear is classified as an advanced persistent threat (APT), which means it employs sophisticated methods to infiltrate its targets. It uses a mix of tactics, including zero-day exploits, spear-phishing, and custom malware, to gain unauthorised access to sensitive information. In the upcoming sections, we will delve deeper into the tactics, techniques, and procedures of APT28.
Since at least 2004, APT28 has set its sights on government, military, and security organisations, particularly those in NATO-aligned countries and the Transcaucasian region. Some of their most significant operations include the hacking of the Democratic National Committee during the 2016 U.S. presidential election and various attacks on international bodies like the World Anti-Doping Agency and the Organisation for the Prohibition of Chemical Weapons. What makes APT28 particularly concerning is their ability to adapt and evolve, making them a persistent threat in the realm of cyber security. Their advanced techniques and strategic targeting continue to challenge organisations around the globe.
Motivations and Targets of APT28
Fancy Bear is a highly active Russian cyber espionage group with a global reach. Their operations align closely with the strategic interests of the Russian government, particularly its military intelligence agency, the GRU.
Motivations
The motivations driving APT28's actions are multifaceted. Primarily, they engage in cyber espionage to gather sensitive information that could further Russia's strategic objectives. This includes monitoring military developments, political activities, and public sentiments in targeted nations. Additionally, their operations often serve to create chaos or influence political outcomes, as evidenced by their involvement in the 2016 U.S. presidential election. By gaining access to and compromising systems across various sectors, APT28 aims not only to collect valuable intelligence but also to undermine trust in democratic institutions and processes. Another reason APT28 remains such a persistent threat in cyber security is their relentless drive to achieve their goals, constantly challenging organisations and governments around the world. As we delve deeper into the tactics, techniques, and procedures employed by APT28, we will gain a clearer understanding of how this group operates and the implications of their actions on global security.
Target Sectors 
APT28 primarily focuses on government institutions, military organisations, and critical infrastructure, particularly in NATO member states and Eastern European countries. Their operations are strategically designed to gather intelligence on defence initiatives, political maneuvers, and security vulnerabilities. By infiltrating these sectors, APT28 aims to understand the operational capabilities and decision-making processes of their targets, providing the Russian government with valuable insights that could influence geopolitical strategies.
These operations aim to gather intelligence that can provide a strategic advantage in geopolitical conflicts, highlighting their intent to manipulate information and disrupt political processes within key institutions.
In this section, we will dive into the notorious world of APT28 and explore the major attacks they have orchestrated over the years. Known for their cunning and sophisticated methods, APT28 has executed a series of high-profile cyber operations that not only reflect their capabilities but also the strategic interests of the Russian government. From targeting political entities to compromising critical infrastructure, APT28's actions show a well-planned approach to cyber espionage. Let's take a closer look at some of the most significant campaigns that have marked APT28's legacy in the cyber landscape.
The DNC Hack
In 2016, the Democratic National Committee (DNC) became the target of a sophisticated cyber intrusion attributed to APT28, also known as Fancy Bear, a notorious Russian cyber espionage group linked to the GRU (Main Intelligence Department). The breach marked a significant event in cyber security history, exposing sensitive information and raising concerns about the integrity of democratic processes. The DNC was first alerted to a potential breach in September 2015 by the FBI, which attributed the intrusion to the Russian government. However, it wasn't until April 30, 2016, that the DNC contacted CrowdStrike, a cyber security firm, to investigate the suspected hack. CrowdStrike began its investigation on May 1, 2016, and detected two advanced threats on the network: COZY BEAR and FANCY BEAR. APT28's breach was traced back to April 2016, prompting a quick effort to remove the intruders within a few days.
APT28 utilised a range of tactics, techniques, and procedures (TTPs) during this campaign, many of which align with the MITRE ATT&CK framework. Their initial access was likely achieved through spear-phishing (T1566), where targeted emails were sent to key personnel, enticing them to click on malicious links or download harmful attachments. This method exploited human mistakes, allowing APT28 to gain access to the DNC's network. Once inside, APT28 employed various types of malware to maintain persistence and navigate the network. They utilised credential dumping (T1003) techniques to harvest usernames and passwords, granting them broader access to sensitive systems.
In terms of malware, APT28 is known to have deployed custom-developed tools like X-Agent, which facilitated remote access to compromised systems. This remote access trojan (RAT) allowed them to monitor network activity, execute commands, and transfer files between the infected host and their command-and-control servers. The DNC hack represents a critical example of APT28's capabilities and intentions.

Presidential Candidate Macron's Campaign 2017 Hack
In 2017, the campaign for French presidential candidate Emmanuel Macron was the target of a sophisticated cyber intrusion attributed to Fancy Bear. This breach occurred in the critical lead-up to the French presidential elections, drawing significant attention to the cyber security threats facing political entities.
The incident involved unauthorised access to sensitive communications and strategies of Macron's campaign team. The attackers aimed to gather confidential information that could potentially influence the electoral process and sway public opinion in favor of certain candidates. This attack was part of a larger effort by APT28 to disrupt political opponents. Although the attack on Macron's campaign did not succeed in derailing his election, it underscored the urgent need for enhanced cyber security measures in political organisations globally.
NATO Joint Air Power Competence Centre 2017 Incident
In 2017, the NATO Joint Air Power Competence Centre (JAPCC) experienced a cyber intrusion attributed to APT28. The attack on the JAPCC was marked by a focused spear-phishing campaign. APT28 targeted specific individuals within the organisation by sending emails that appeared legitimate but contained malicious links or attachments. These deceptive communications were designed to compromise the systems of unsuspecting personnel. Once inside the network, the attackers deployed custom malware to establish persistence and facilitate the exfiltration of sensitive information, following patterns observed in their previous operations.
Technical investigations into the incident indicated that APT28 employed various techniques, including credential dumping and lateral movement, to escalate their privileges and access critical systems. Such tactics highlight the group's sophisticated approach to cyber espionage, reinforcing the necessity for robust cyber security measures, especially within organisations involved in defence and military operations. The implications of the JAPCC incident were significant, triggering concerns about the integrity of sensitive military information and the potential impact on NATO's operational effectiveness. This breach serves as a potent reminder of the evolving threat landscape and the critical need for continuous vigilance and the implementation of advanced defensive strategies to guard against state-sponsored cyber threats.
We have reviewed three notable incidents linked to APT28. In the cases described earlier, we didn't dive into the technical specifics. Those details will be explored in the upcoming sections, where we'll discuss their tools and techniques in depth. Stay tuned for more insights on how APT28 operates behind the scenes. Below are a few other intriguing attacks attributed to this group that you should be aware of:
- German Bundestag (2015): Compromised to gather intelligence on political activities.
- French TV5 Monde (2015): Targeted to disrupt media operations and control narratives.
- Democratic National Committee (DNC) (2016): Infiltrated to influence the U.S. presidential election.
- World Anti-Doping Agency (WADA) (2016): Breached to obtain sensitive information related to sports governance.
- U.S. Nuclear Facilities: Attacks aimed at critical infrastructure to gather intelligence.
- Ukraine's Ministry of Defence: Targeted to monitor military developments amid ongoing conflict.
- NATO and NATO-aligned organisations: Attacked to gain insights into defence strategies and operations.
- Political parties and candidates in France: Targeted to influence the outcome of elections, including the campaign of Emmanuel Macron.
- The Organisation for Security and Co-operation in Europe (OSCE): Infiltrated to disrupt diplomatic efforts and gather intelligence on international negotiations.
- Cyber security firms: Compromised to access information about countermeasures against cyber threats.
Here, you can see a map of APT28's known victims across different regions and sectors.
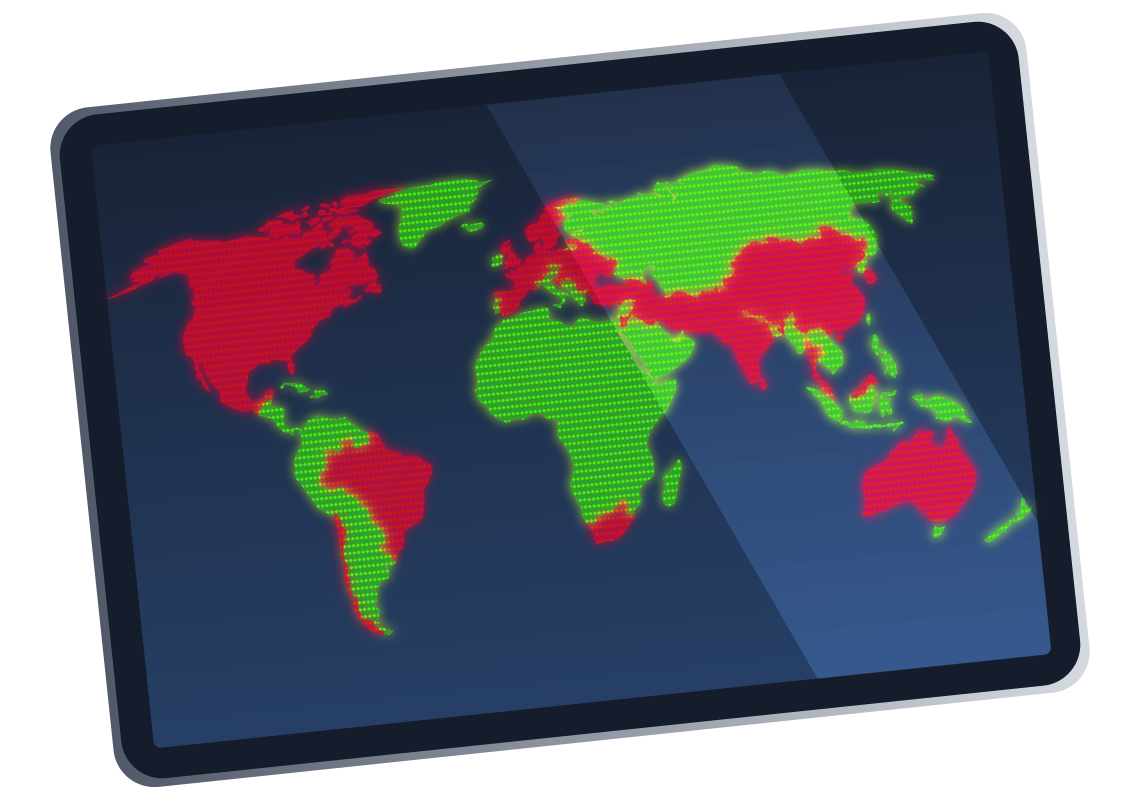
This section will explore the initial access techniques associated with APT28's activities across various operations. We’ll dive into their strategies to breach targeted organisations and how these methods align with their broader tactics. From phishing attacks to exploiting vulnerabilities, these techniques have allowed APT28 to gain a foothold in high-profile networks, setting the stage for more advanced malicious actions.
Phishing Campaigns
Phishing is a technique used by cyber adversaries to deceive individuals into providing sensitive information by pretending to be a trustworthy source. Typically delivered through email, these fraudulent messages often contain malicious links or attachments. APT28 frequently employs phishing to gain initial network access, exploiting human trust to bypass security measures.
Spear-phishing Attachment - T1566.001 MITRE ID
APT28 utilises spear-phishing emails with malicious Microsoft Office and RAR attachments to gain access to target systems. These attachments exploit vulnerabilities, deceiving victims into opening them and enabling unauthorised access to their networks. In February 2018, APT28 targeted two government institutions related to international relations using spear-phishing emails. The emails, spoofed to appear from a legitimate source (Jane's 360 defence events), contained an Excel attachment disguised as a calendar of events. The attachment used a malicious macro script that hid its content, prompting victims to enable macros. Once enabled, the macro changed the font colour, revealing the document's content, which contained several anomalies indicative of malicious intent. Click to enlarge image.

In another attack, APT28 initiated the Dealer’s Choice campaign in early 2017, marked by a series of spear-phishing attempts targeting military and defence-related organisations. These attacks utilised multiple stages of emails containing Flash exploits that led to the deployment of Carberp-based JHUHUGIT downloaders and subsequent malware. Analysts noted that many targets were linked, even indirectly, to Ukraine and NATO interests, highlighting APT28's persistent focus on geopolitical objectives.
During the campaign, APT28 often pretended to be their targets, making their spear-phishing efforts more successful. By impersonating trusted contacts, they were able to break into networks and access sensitive information.
Spear-phishing Link - T1566.001 MITRE ID
Spear-phishing attacks using links involve sending emails with malicious URLs that often appear to be from legitimate sources. Attackers may use URL-shortener services to disguise these links, redirecting victims to credential harvesting sites. By leveraging social engineering tactics, they manipulate targets into clicking these links, leading to unauthorised access and data theft. This method enables attackers to bypass security measures that focus on attachment scanning, making it a prevalent technique in cyber espionage campaigns.
Spear-phishing attacks using links exploit user trust through social engineering, a technique frequently employed by APT28. One notable example is IRON TWILIGHT's email credential targeting system, which directs victims to fake login pages that imitate legitimate webmail services like Gmail.
In a specific campaign, researchers tracked APT28's use of the Bitly link-shortening service to target thousands of Gmail users, including military personnel, government employees, and journalists. This method allowed attackers to capture credentials efficiently and maintain persistent access to compromised accounts through OAuth features.
Valid Accounts - T1078 MITRE ID
APT28 has leveraged stolen valid credentials for initial access to European political entities, enabling them to gain access to networks effectively. Using credentials obtained from phishing attacks and the dark web, they targeted various government agencies and political organisations through stealthy measures. This tactic allowed for lateral movements within networks from a future perspective, leading to the collection of sensitive information. Such methods highlight the need for robust security measures against credential theft.
Zero-Day Exploits
A zero-day exploit takes advantage of a previously unknown vulnerability in software, allowing attackers to execute malicious code before the vendor has released a patch. APT28 has demonstrated a strong capability to leverage zero-day vulnerabilities to maximise its effectiveness in cyber attacks.
- CVE-2015-3043: APT28 has used this vulnerability, a buffer overflow in Adobe Flash Player, which allows remote code execution. When users are deceived into visiting a malicious website, the Flash exploit can execute shellcode that downloads and runs additional malware. This particular exploit exemplifies APT28's focus on using widely adopted software with significant user bases to increase their attack surface.
- CVE-2015-1701: This unpatched local privilege escalation vulnerability in the Windows kernel is exploited by APT28's payload after executing the Flash exploit. It enables attackers to elevate their privileges to the level of the System process, granting them full control over the compromised system. This two-step approach—first gaining initial access and then escalating privileges—illustrates the tactical sophistication of APT28.
APT28 has also been reported to utilise other zero-day vulnerabilities over the years. For example, they exploited vulnerabilities in Microsoft Office and the Windows operating system, allowing for initial access or privilege escalation in various targeted environments. List of known Zero-Days associated with APT28(non-exhaustive): CVE-2015-2590,CVE-2017-0261, CVE-2017-0262, CVE-2017-0263, CVE-2015-2424, CVE-2016-7855, CVE-2016-0167,CVE-2022-30190.
Exploitation of Public Facing Applications - T1190 MITRE ID
Initial Access through Public Exploits: APT28 has been known to leverage vulnerabilities in public-facing applications to gain initial access to target systems. By exploiting weaknesses in widely used software, the group can execute malicious payloads and gain privileged access to sensitive environments. Examples of Exploited Vulnerabilities:
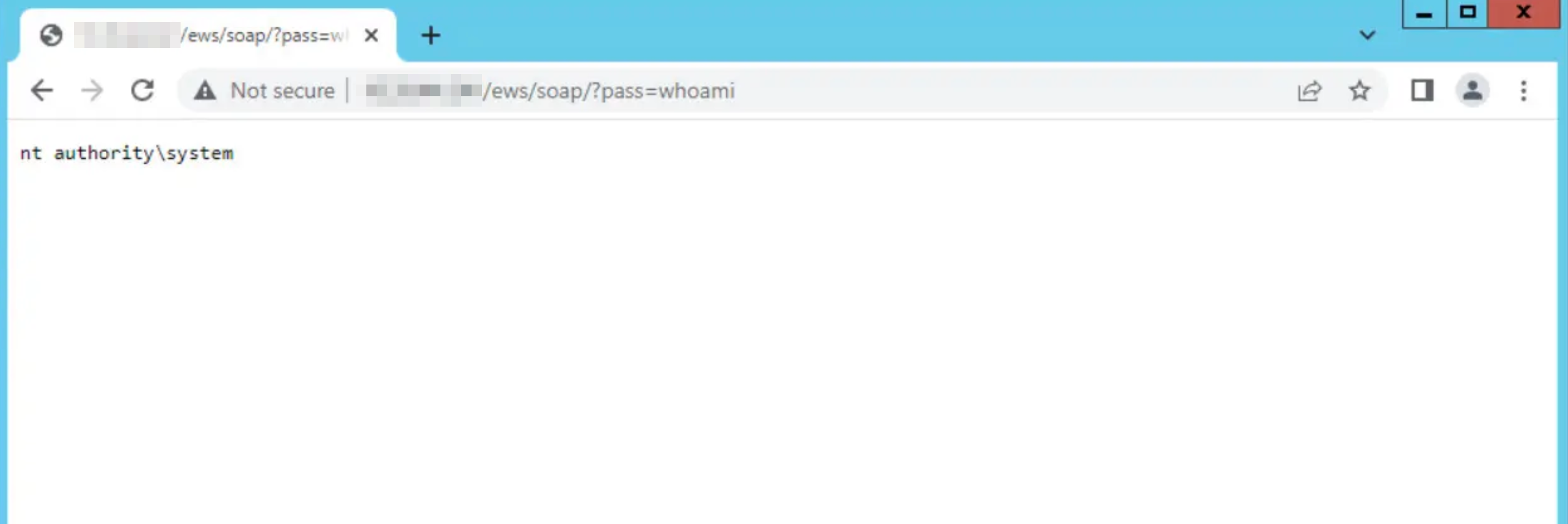
- CVE-2020-0688: This CVE is a critical vulnerability affecting Microsoft Exchange Server. This flaw allows attackers to bypass authentication and gain remote code execution on vulnerable servers. APT28 exploited this vulnerability to take control of Exchange Servers, enabling them to deploy additional malware and establish persistence within targeted networks. The exploit takes advantage of improper validation of the input received by the application, making it a valuable entry point for attackers. You can see exploitetion results, also server response when CVE-2020–0688 is exploited.
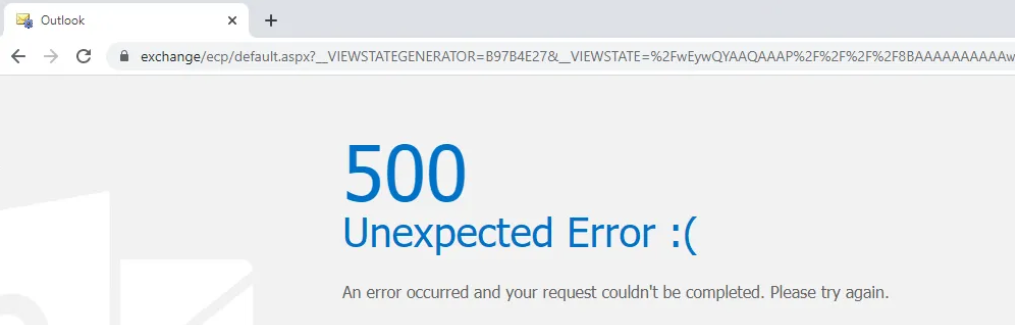

- CVE-2020-17144: Another significant vulnerability exploited by APT28 is CVE-2020-17144, also affecting Microsoft Exchange Server. This vulnerability enables attackers to execute code with elevated privileges on the server, which can lead to a full compromise of the affected system. The exploitation of this vulnerability typically involves sending specially crafted requests to the Exchange Server, resulting in unauthorised access and control. On the screen, you can observe the exploitation of the CVE-2020-17144 vulnerability, where the attacker gains SYSTEM privileges.
Here, we discuss the main initial access TTPs performed by APT28. Now, let's move on to the question part to test your understanding of these techniques.
Now that we've covered how APT28 gains initial access to their targets, let's explore the persistence mechanisms they use to maintain long-term access within victim networks.
Boot or Logon Initialisation Scripts - T1037 MITRE ID
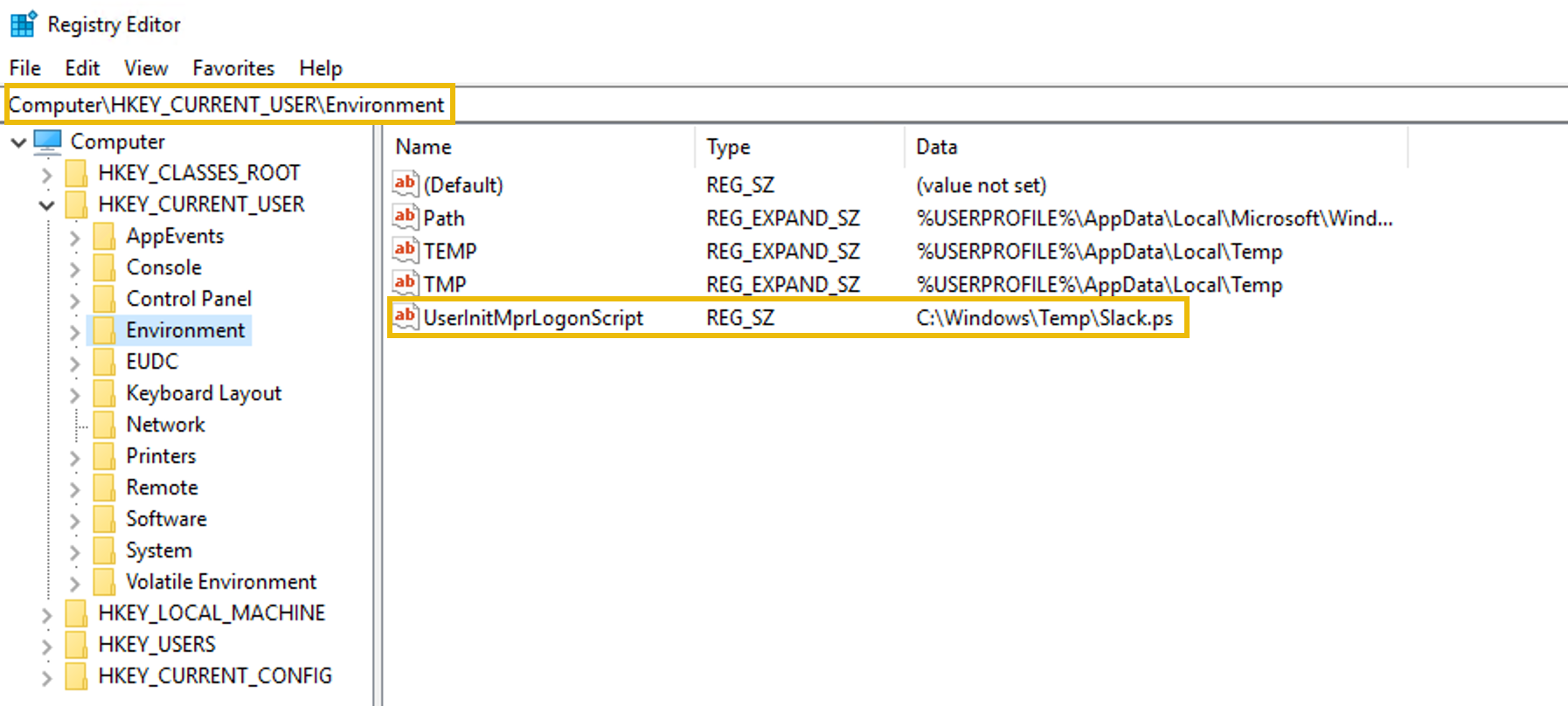
One prevalent persistence technique employed by APT28 is Boot or Logon Initialisation Scripts. This method enables threat actors to maintain access to the victim's system by executing malicious code during the system's startup or user logon process. By modifying these startup scripts, APT28 ensures that their malware or tools are automatically executed each time the system boots or a user logs in. A specific implementation of this technique used by APT28 can be observed in the registry key located at HKCU\Environment\UserInitMprLogonScript. This key is utilised to specify scripts that run at user logon, allowing APT28 to establish persistence within the victim's environment. On the screen, you can observe how this persistence mechanism is represented within the Registry Editor.
Boot or Logon Autostart Execution - T1547 MITRE ID
Another prevalent persistence technique employed by APT28 is Boot or Logon Autostart Execution. This method enables threat actors to ensure their malicious payloads are executed automatically at system boot or during user logon. By modifying various autostart locations within the Windows environment, APT28 can maintain a persistent presence on the victim's system.
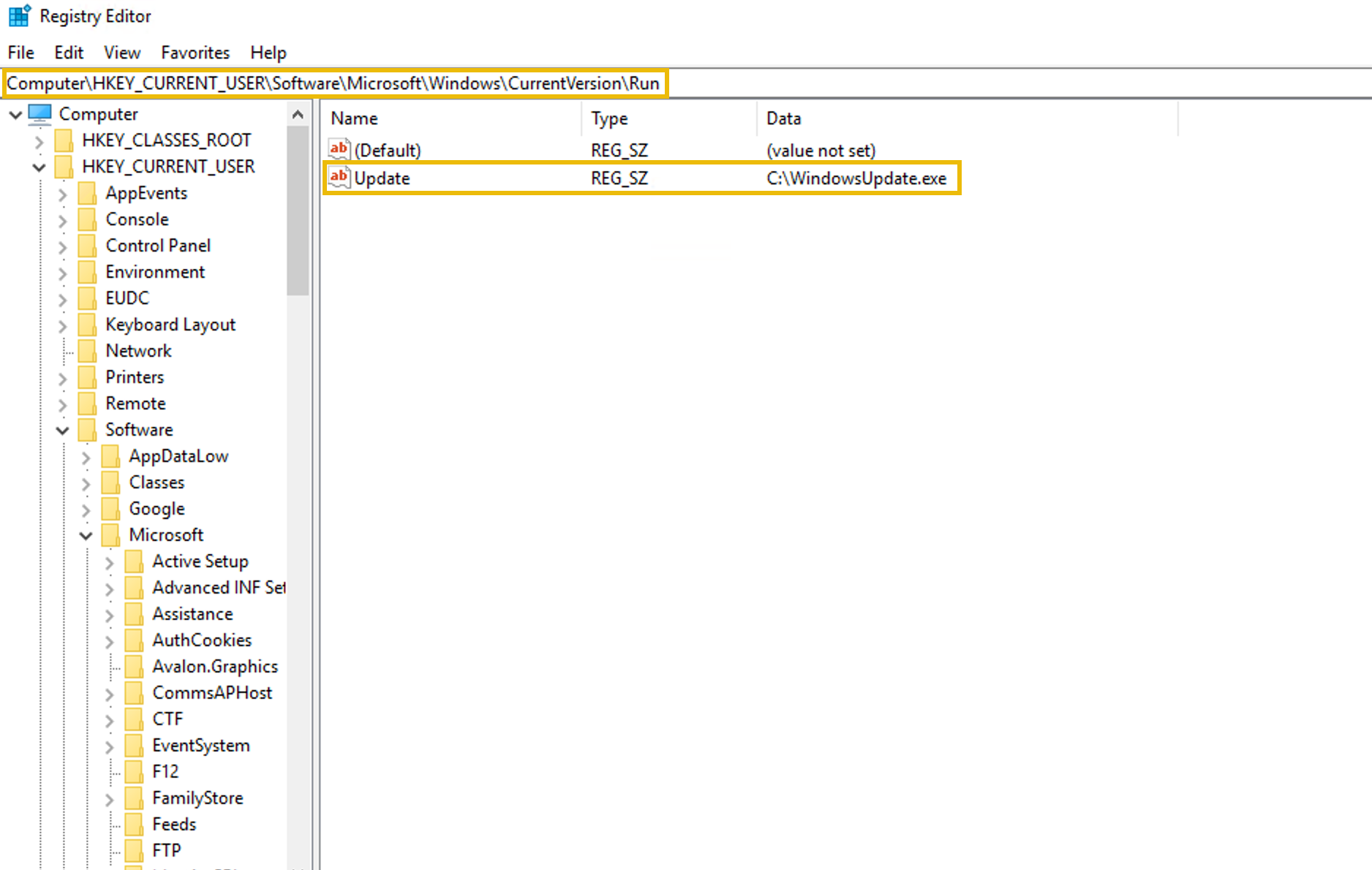
For instance, APT28 may leverage registry keys located in HKCU\Software\Microsoft\Windows\CurrentVersion\Run or utilize the Startup folder to place executable files that launch upon user logon. This approach makes it easier for them to run their malware and lowers the chances of being detected, as they can create entries that look like regular system processes.
On the screen, you can see how this persistence mechanism is represented in the Registry Editor, showcasing how APT28 integrates their malicious activities within the normal operation of the system.
Component Object Model Hijacking - T1546.015 MITRE ID
APT28 has been known to use Component Object Model Hijacking as a stealthy persistence technique. By hijacking COM objects, they can modify the registry to ensure malicious code is loaded whenever a legitimate process invokes a COM object. This provides the attackers with persistent access to the system, as their code runs unnoticed during normal system operations.
The Windows COM Registry database contains mapping information for every COM object, which the system uses to locate and load COM objects on disk. Attackers such as APT28 leverage this by manipulating the Class ID (CLSID) entries in the registry, redirecting legitimate COM objects to execute their malicious binaries.
Two registry locations commonly associated with this attack are:
- HKEY_CLASSES_ROOT\CLSID
- HKEY_CLASSES_ROOT\WOW6432Node\CLSID
These keys store the CLSID, a globally unique identifier (GUID) that represents a specific COM class. For example, the CLSID {71A24DD5-P61A-448B-8C32-13424B88AFB8} maps to a legitimate COM object in the system. However, APT28 modifies these entries to point to malicious binaries. For example:
- HKEY_CLASSES_ROOT\CLSID{79ECA078-17FF-726B-E811-213280E5C831}
- HKEY_CLASSES_ROOT\WOW6432Node\CLSID{79FEACFF-FFCE-815E-A900-316290B5B738}
In these cases, APT28 could change the values of these CLSIDs to execute their own malware when the system or applications invoke these objects, ensuring their malicious payload runs automatically. On the screen, you can see how this persistence mechanism appears within the Registry Editor, demonstrating how these keys are modified by APT28 to maintain persistence on a compromised system. In the below image, note 3 points of interest: The full registry key path (1), the CLSID of the COM object (2), and the file path to the COM object's implementation on disk (3), typically a DLL (or .ocx file)./p>

Office Application Startup: Office Test - T1137.002 MITRE ID
APT28 has employed a persistence technique targeting Microsoft Office applications, specifically utilizing the registry key path HKCU\Software\Microsoft\Office test\Special\Perf. This method ensures that malicious DLLs are loaded each time an Office application, like Word, is started, allowing attackers to maintain access.
In recent targeted attacks by APT28, they used a delivery document that created the aforementioned registry key to load a malicious DLL whenever a Microsoft Office application was opened. This technique was initially seen as novel, but further research showed it had been documented by other researchers in the past, suggesting APT28 adopted it into their operations.
How the Attack Works
- Registry Key Creation: The document creates the key HKCU\Software\Microsoft\Office test\Special\Perf. This key isn’t present on a default installation of Microsoft Office, making it easier for attackers to introduce their malware.
- DLL Loading: When a user opens a Microsoft Word document, Word’s legitimate process wwlib.dll queries this key to load the DLL referenced within. A malicious DLL is loaded using LoadLibraryW, allowing the attacker’s code to execute each time Word or another Office application is started.
- Malware Execution: In the Fancy Bear attacks, this APT placed their loader Trojan btecache.dll within the key, which then loaded the svchost.dll from C:\ProgramData. This second DLL contained the actual payload that ran while the Office application remained open.
APT28 places the key in HKCU, where only regular user privileges are needed to modify it, avoiding the need for admin access that would be required in the HKLM hive. Since the malicious DLL is loaded by a legitimate Office application process, this method makes detection more difficult, as the malicious activity blends in with normal operations.
To wrap up the persistence section, we have discussed several key techniques used by APT28 to establish long-term access on compromised systems.
There are additional persistence techniques employed by APT28 that we won't cover immediately, leaving them for self-study and further exploration.
Since we've covered initial access and persistence, what's next? Once an APT is inside the network, the next logical step is to elevate their privileges to gain deeper control over the system. This section will explore the primary techniques attackers use to escalate their privileges and strengthen their foothold in the environment. APT28, like many advanced threat actors, often leverages system misconfigurations to escalate privileges. Misconfigurations are common in many environments, and APT28 exploits them to gain higher-level access. These vulnerabilities are crucial because, once exploited, they allow attackers to move laterally across the network, gain administrative rights, and bypass security controls, making their presence harder to detect and remove.
One of the reasons APT28 frequently exploits system misconfigurations is that these weaknesses are often overlooked in system hardening processes. Properly configuring services, files, and registry permissions requires thorough attention to detail, and even small oversights can be exploited for privilege escalation.
Unquoted Service Paths
An unquoted service path is a common misconfiguration that APT28 can use to gain elevated privileges. When a service has an unquoted path in its configuration, Windows may misinterpret spaces in the path and execute an unintended binary. Attackers can place their malicious executables in these directories, ensuring that their code is executed with the same privileges as the service - often SYSTEM-level privileges.
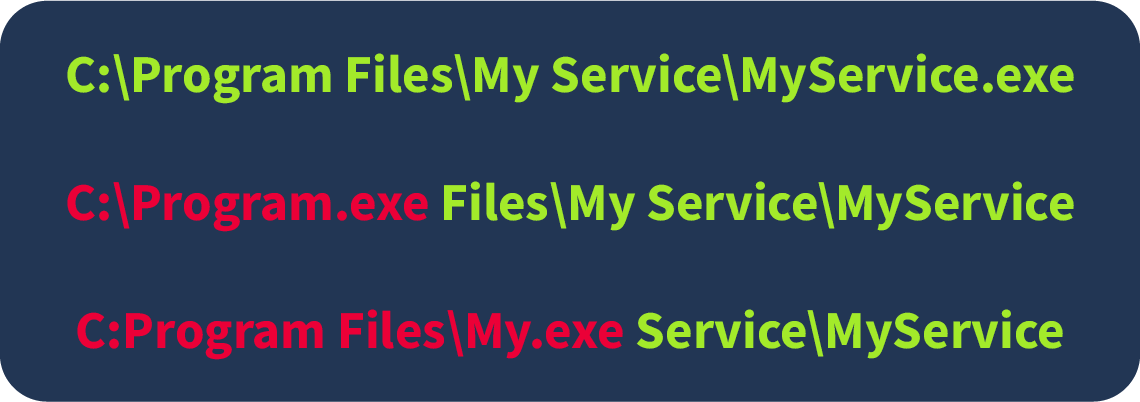
For example, a service path like C:\Program Files\My Service\MyService.exe without quotation marks may be interpreted as an attempt to run C:\Program.exe or C:\Program Files\My.exe if such a file exists. This provides an opportunity for the attacker to inject their malicious payload and run it with elevated privileges.
Weak Service Permissions
Weak service permissions are another key misconfiguration that APT28 exploits. If a service is misconfigured to allow overly permissive access control, attackers can modify the service configuration to point to their own malicious binaries. This allows them to control when the service starts or stops and ensures their malware is executed with higher privileges. This type of misconfiguration can occur if services are not properly secured or if default permissions are not tightened during deployment.
So, how can an attacker exploit these vulnerabilities?
Below, we explain how to use weak service permissions to escalate privileges via Cobalt Strike. Please note that this is just an example for a better understanding of this technique.
Step 1: Identify Modifiable Services
The first step involves scanning the system for services that can be modified. Using, for example, SharpUp, we can identify which services have weak permission:
c2> execute-assembly C:\Tools\SharpUp\SharpUp\bin\Release\SharpUp.exe audit ModifiableServices
=== Modifiable Services ===
Service 'WeeklyTask' (State: Running, StartMode: Auto)
In this case, WeeklyTask is found to be modifiable.
Step 2: Check Service Permissions
Next, we need to check the permissions associated with the service to see if we can exploit them.
c2> powershell-import C:\Tools\Get-ServiceAcl.ps1
c2> powershell Get-ServiceAcl -Name WeeklyTask | select -expand Access
ServiceRights : ChangeConfig, Start, Stop
AccessControlType : AccessAllowed
IdentityReference : NT AUTHORITY\Authenticated Users
IsInherited : False
InheritanceFlags : None
PropagationFlags : None
Here, we can see that Authenticated Users have the rights to ChangeConfig, Start, and Stop the service.
Step 3: Validate Current Binary Path
To understand how we can exploit this, we need to check the current binary path of the service.
c2> sc qc WeeklyTask
BINARY_PATH_NAME : "C:\Program Files\Services\Update.exe"
We have successfully displayed the current path of the WeeklyTask service.
Step 4: Upload Malicious Payload
Next, we upload a malicious payload to the system that we will configure the service to execute. We’ll place our payload in a temporary directory.
Step 5: Change the Service's Binary Path
Now that we have our payload uploaded, we can change the service's binary path to point to our malicious executable.
c2> sc config WeeklyTask binPath= C:\Temp\Teams.exe
It's essential to confirm that the binary path has been successfully updated.
Step 6: Stop and Start the Service
To execute our malicious payload, we need to stop the service and then start it again.
c2> run sc stop WeeklyTask
c2> run sc start WeeklyTask
Here, we reviewed how APTs and other threat actors can exploit weak service permissions. By identifying modifiable services like WeeklyTask, attackers can change the service's binary path to execute malicious payloads, gaining elevated privileges and maintaining persistence. This underscores the need for proper service permission configurations.
Access Token Manipulation: Token Impersonation/Theft - T1134.001 MITRE ID
Access token manipulation is a technique that allows attackers to alter or abuse access tokens to gain unauthorised privileges on a system. In Windows, access tokens are used to represent the security context of a user or process, determining what resources and actions they can access. By manipulating these tokens, attackers can impersonate users with higher privileges or bypass security restrictions. Below is a diagram that outlines how this process works. We won’t go into depth, but it’s meant to provide a clearer understanding.
APT28 has been known to leverage access token manipulation to enhance their foothold within a compromised environment. This technique enables them to escalate privileges and execute malicious actions without being detected. By obtaining a valid access token from a process running with elevated privileges, APT28 can create a new process that runs with those same privileges, effectively allowing them to perform tasks that would typically require administrator rights.
For example, APT28 may inject a malicious payload into a running process that has a high-privilege access token. Once injected, they can execute commands as if they were the high-privileged user, enabling actions such as modifying system configurations, accessing sensitive data, or disabling security measures. This method not only allows them to execute their attacks more effectively but also helps maintain their presence on the system, making it harder for defenders to identify and mitigate their activities.
In addition to the techniques discussed, APT28 has also been known to exploit various vulnerabilities for privilege escalation, along with numerous other system misconfigurations that we cannot cover in detail here.
Once threat actors gain elevated privileges within a target system, their next objective is often lateral movement - expanding their access to other systems within the network. This allows them to further exploit resources, gather intelligence, and maintain persistence. APT28 employs various lateral movement techniques that facilitate this process, enabling them to navigate through networks stealthily and efficiently.
In this section, we will explore some common lateral movement techniques, how APT28 utilises them, and the implications for network security.
Pass the Hash - T1550.002 MITRE ID
APT28 has leveraged the Pass-the-Hash technique for lateral movement within compromised networks. This method allows attackers to authenticate to other systems by using an NTLM hash instead of the plaintext password itself.
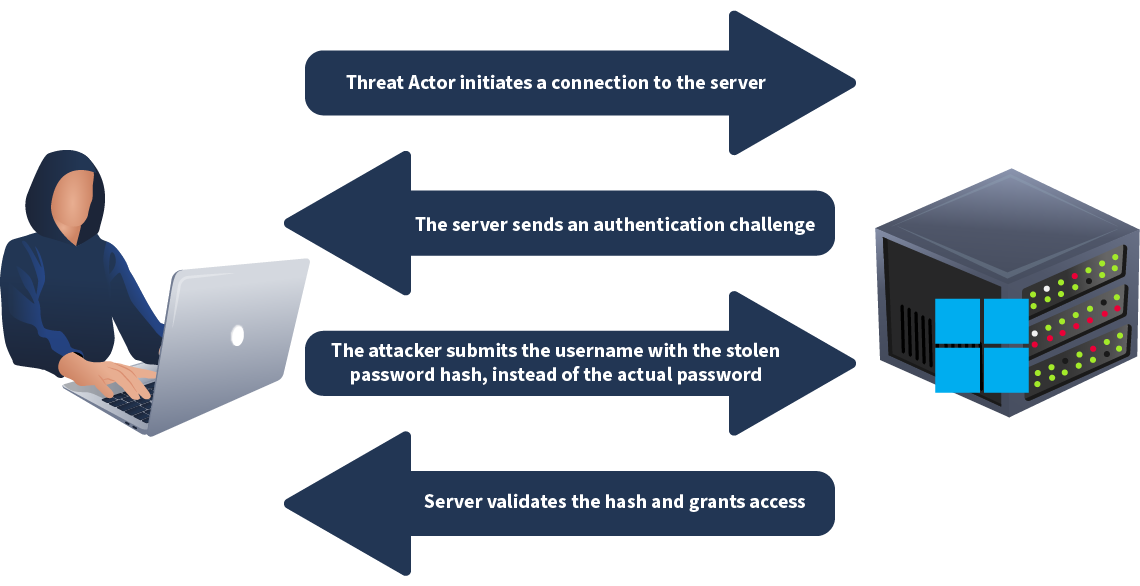
APT28 typically starts by stealing NTLM hashed credentials from a compromised machine, often by exploiting weak security configurations or leveraging tools that extract password hashes from memory. Once the hashes are acquired, attackers can use them to authenticate against other machines without needing to decrypt the actual passwords. This enables them to move laterally across the network, accessing systems and services as if they were legitimate users. APT28 may utilise various tools and scripts designed for PTH attacks, facilitating rapid lateral movement. Common tools include Mimikatz and others, which can execute commands remotely using the stolen NTLM hashes.
Windows SMB Remote Code Execution - T1210 MITRE ID
APT28 targets specific vulnerabilities within the Server Message Block (SMB) protocol. For example, vulnerabilities like EternalBlue (CVE-2017-0144) allow attackers to send specially crafted packets to a vulnerable SMB server, enabling remote code execution. After identifying vulnerable systems within the network, APT28 can exploit these vulnerabilities to execute code on the target machine without requiring user interaction. This often involves sending malicious payloads that exploit the vulnerability in the SMB service. Once the code execution is successful, the attackers can gain administrative access to the compromised machine. This access allows them to install malware, create backdoors, and move laterally to other systems within the network. APT28 may use various exploitation frameworks or scripts to automate the process of scanning for vulnerable SMB services and executing the required payloads. By leveraging SMB Remote Code Execution vulnerabilities, APT28 can quickly and effectively expand their control over a network, posing significant risks to the confidentiality, integrity, and availability of the targeted environment.
Now that APT28 has moved laterally across the network and gained control of key systems, their next step is to gather sensitive data and exfiltrate it back to their infrastructure. APT28 is known for meticulously searching through compromised systems to collect valuable intelligence, such as emails, documents, credentials, and network configurations. They often target file shares, databases, and communications for critical data. Once the data is gathered, APT28 focuses on hiding the exfiltration process, using legitimate services and encrypted channels to avoid detection. APT28's data collection and exfiltration techniques focus on gathering high-value information that can serve their long-term espionage goals. Let’s break down some examples of the type of data they tend to target, how they collect it, and why it's crucial: 
- Government and Military Documents: They steal classified reports, military plans, and intelligence data to gain strategic insights.
- Emails and Communications: APT28 intercepts emails and sensitive communications from diplomats, government officials, and political figures to gather intelligence.
- Login Credentials: They collect usernames, passwords, and tokens to gain deeper access to systems for long-term operations.
- Network and System Configurations: They gather system files, firewall rules, and network maps to evade detection and identify vulnerabilities.
- Intellectual Property: APT28 targets corporate secrets, including research, designs, and technology, especially in the aerospace and defence sectors.
APT28 employs several advanced tools to collect and exfiltrate sensitive data from targeted systems, focusing on stealth and efficiency. Here’s a breakdown of some of their key tools and how they use them:
- Agent (Sofacy or Sednit): X-Agent is one of APT28’s primary data collection tools, capable of keylogging, capturing screenshots, and stealing files. It was infamously used in the 2016 breach of the Democratic National Committee (DNC), where APT28 gathered emails and sensitive documents, which were later exfiltrated and leaked.
- X-Tunnel: This tool facilitates encrypted communication channels for exfiltrating stolen data. X-Tunnel was also deployed in the DNC hack to send the stolen data back to APT28-controlled servers, bypassing standard detection mechanisms by using encrypted traffic.
- Zebrocy: A lightweight downloader and reconnaissance tool, Zebrocy was used in spear-phishing campaigns targeting NATO and Eastern European organisations. It helped APT28 gather initial data from compromised systems, such as credentials and system configurations, for further exploitation and lateral movement.
- USBStealer: USBStealer is designed for air-gapped networks and was notably used in an operation against Ukrainian military forces. APT28 used it to collect classified data from machines that were not connected to the internet, leveraging infected USB devices to bridge the gap and exfiltrate data when those devices were connected to internet-facing systems.
Great job completing this room! You’ve learned a lot about APT28 and how they operate. Here’s a quick recap of what you covered:
- APT Overview: You gained insights into what APTs are and how they operate within the cyber threat landscape.
- APT28 Profile: We discussed the background of APT28, also known as Fancy Bear, including their origins and affiliations.
- Tactics, Techniques, and Procedures: You examined the specific TTPs used by APT28, helping you recognise the signs of similar threats in the wild.
Stay tuned for the next installment of the saga about APT28 - very soon, you’ll step into a hands-on DFIR room with exercises where you can put your knowledge of Fancy Bear’s behavior into practice.
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in
