To access material, start machines and answer questions login.
Some employees from your company reported that they can’t log into Outlook. The Exchange system admin also reported that he can’t log in to the Exchange Admin Center. After initial triage, they discovered some weird readme files settled on the Exchange server.
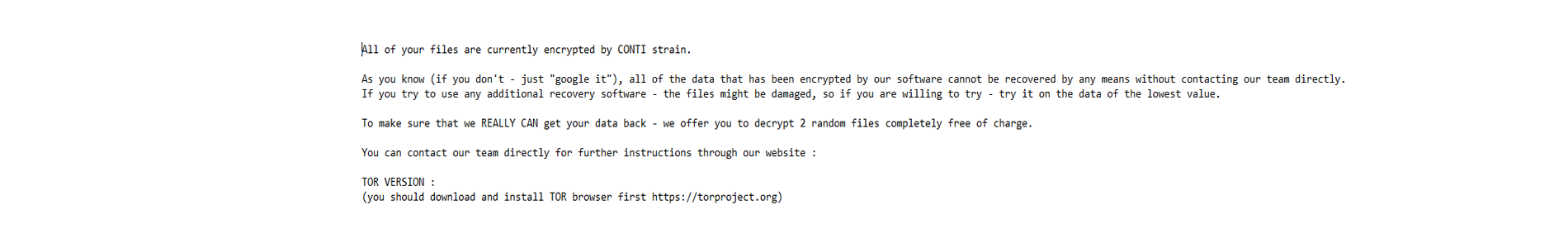
Below is a copy of the ransomware note.
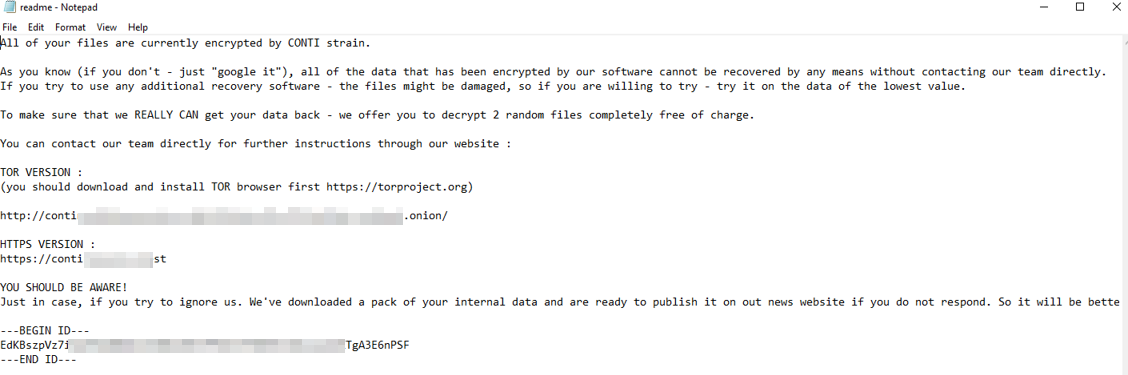
Warning: Do NOT attempt to visit and/or interact with any URLs displayed in the ransom note.
Read the latest on the Conti ransomware here.
Connect to OpenVPN or use the AttackBox to access the attached Splunk instance.
Splunk Interface Credentials:
Username: bellybear
Password: password!!!
Splunk URL: http://MACHINE_IP:8000
Special thanks to Bohan Zhang for this challenge.
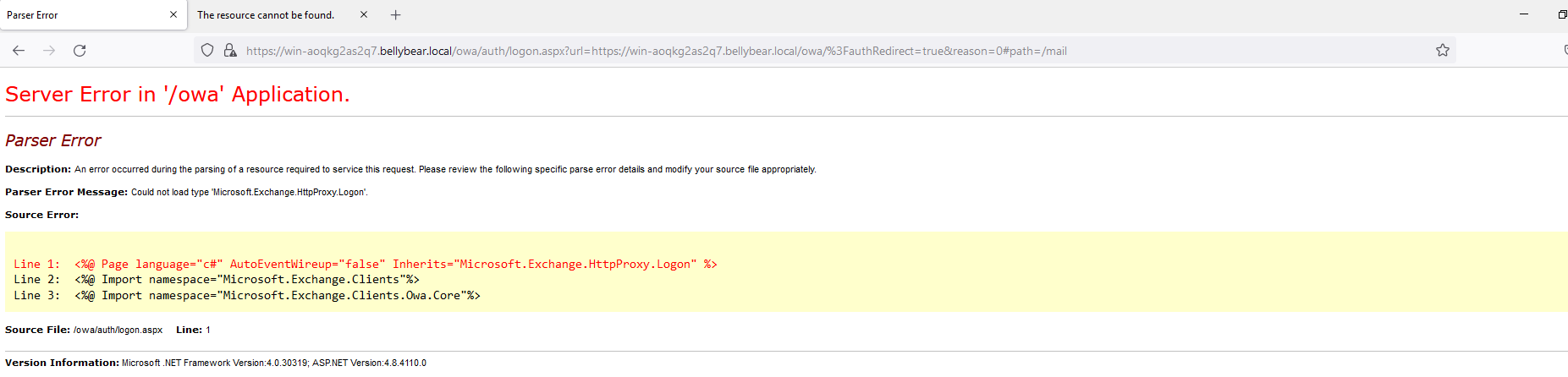
Below are the error messages that the Exchange admin and employees see when they try to access anything related to Exchange or Outlook.
Exchange Control Panel: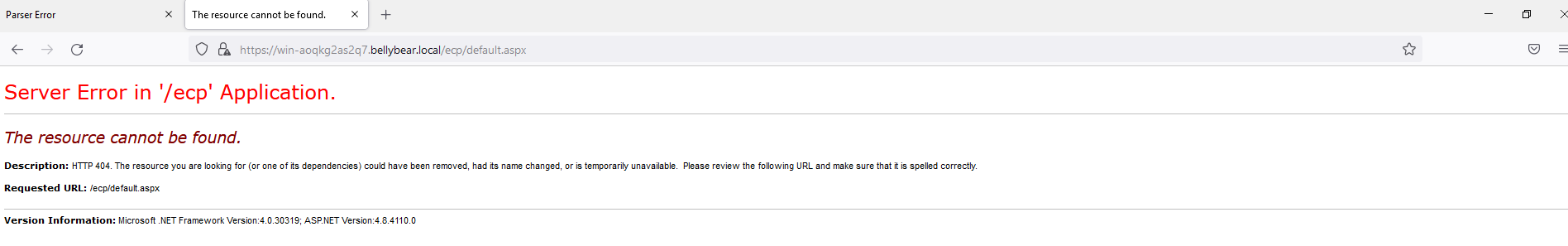
Outlook Web Access:
Task: You are assigned to investigate this situation. Use Splunk to answer the questions below regarding the Conti ransomware.
What is the Sysmon event ID for the related file creation event?
Can you find the MD5 hash of the ransomware?
What file was saved to multiple folder locations?
What was the command the attacker used to add a new user to the compromised system?
The attacker migrated the process for better persistence. What is the migrated process image (executable), and what is the original process image (executable) when the attacker got on the system?
The attacker also retrieved the system hashes. What is the process image used for getting the system hashes?
What is the web shell the exploit deployed to the system?
What is the command line that executed this web shell?
What three CVEs did this exploit leverage? Provide the answer in ascending order.
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in