To access material, start machines and answer questions login.

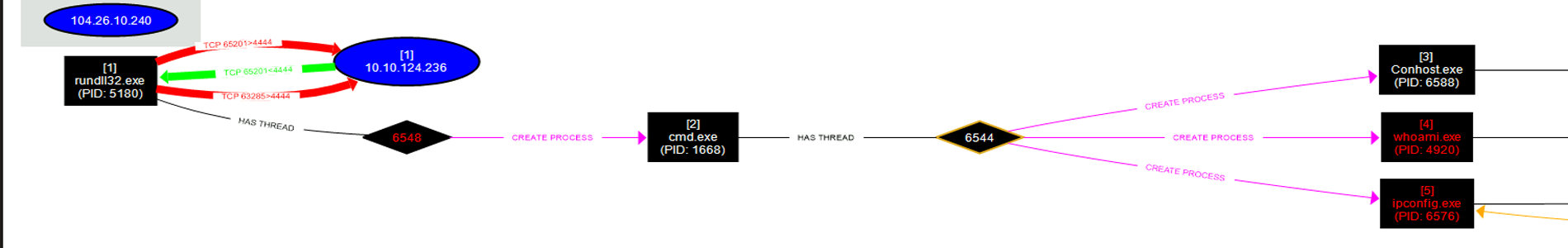
The firewall alerted the Security Operations Center that one of the machines at the Sales department, which stores all the customers' data, contacted the malicious domains over the network. When the Security Analysts looked closely, the data sent to the domains contained suspicious base64-encoded strings. The Analysts involved the Incident Response team in pulling the Process Monitor and network traffic data to determine if the host is infected. But once they got on the machine, they knew it was a ransomware attack by looking at the wallpaper and reading the ransomware note.
Can you find more evidence of compromise on the host and what ransomware was involved in the attack?
Provide the two PIDs spawned from the malicious executable. (In the order as they appear in the analysis tool)
Provide the full path where the ransomware initially got executed? (Include the full path in your answer)
What are the IPs of the malicious domains? (no space in the answer)
Provide the user-agent used to transfer the encrypted data to the C2 channel.
Provide the cloud security service that blocked the malicious domain.
Provide the name of the bitmap that the ransomware set up as a desktop wallpaper.
Find the PID (Process ID) of the process which attempted to change the background wallpaper on the victim's machine.
The ransomware mounted a drive and assigned it the letter. Provide the registry key path to the mounted drive, including the drive letter.
Now you have collected some IOCs from this investigation. Provide the name of the ransomware used in the attack. (external research required)
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in