Task 1Introduction
Task includes a deployable machine
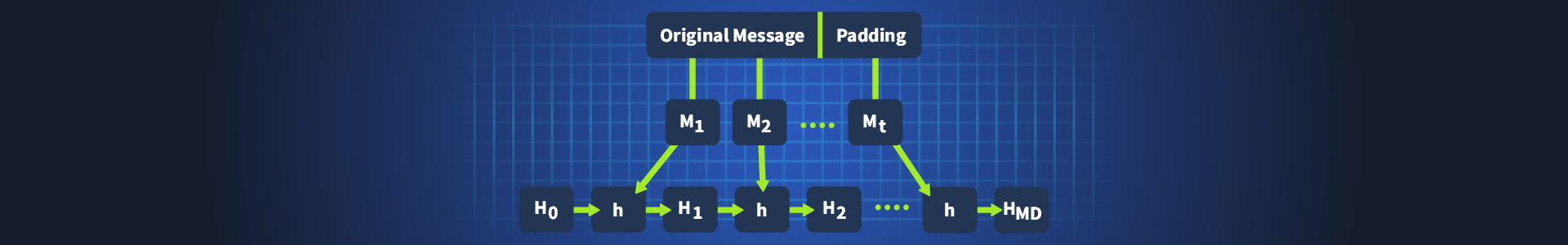
Task 2Hash Functions
Task 3Hashing Internals
Task 4Understanding Length Extension Attacks
Task 5Practical - Attacking Signatures
Task 6Practical - Modifying a Signed Cookie
Task 7Mitigation Techniques
Task 8Conclusion
Ready to learn Cyber Security? Create your free account today!
The Length Extension Attacks room is only available for premium users. Signup now to access more than 500 free rooms and learn cyber security through a fun, interactive learning environment.
Already have an account? Log in