To access material, start machines and answer questions login.

Three machines in the Finance department at Pfeffer PLC were compromised. We suspect the initial source of the compromise happened through a phishing attempt and by an infected USB drive. The Incident Response team managed to pull the network traffic logs from the endpoints. Use Brim to investigate the network traffic for any indicators of an attack and determine who stands behind the attacks.
NOTE: DO NOT directly interact with any domains and IP addresses in this challenge.
Deploy the machine attached to this task; it will be visible in the split-screen view once it is ready.
If you don't see a virtual machine load then click the Show Split View button.

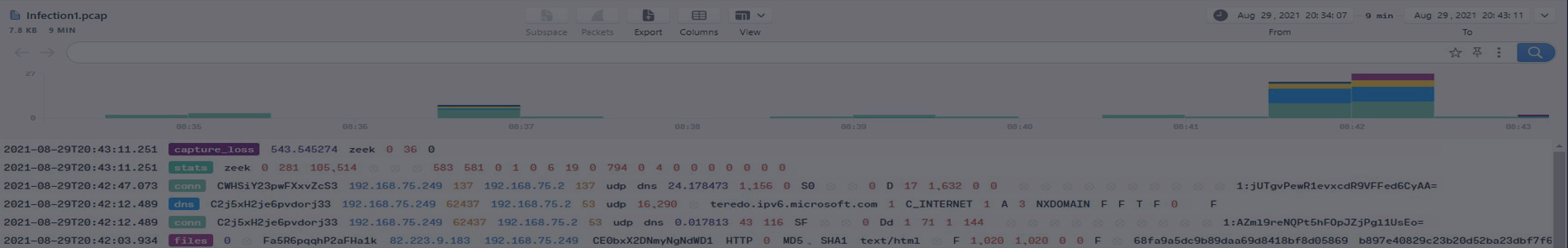
Start by loading the Infection1 packet capture in Brim to investigate the compromise event for the first machine. All the PCAPs can be found here: /home/ubuntu/Desktop/PCAPs
Note: For questions that require multiple answers, please separate the answers with a comma.
Provide the victim's IP address.
The victim made a successful HTTP connection to one of the domains and received the response_body_len of 1,309 (uncompressed content size of the data transferred from the server). Provide the domain and the destination IP address.
How many unique DNS requests were made to cab[.]myfkn[.]com domain (including the capitalized domain)?
Provide the URI of the domain bhaktivrind[.]com that the victim reached out over HTTP.
Provide the IP address of the malicious server and the executable that the victim downloaded from the server.

Please, navigate to the Infection2 packet capture in Brim to investigate the compromise event for the second machine.
Note: For questions that require multiple answers, please separate the answers with a comma.
Provide the IP address of the victim machine.
How many POST connections were made to the IP address in the previous question?
Provide the domain where the binary was downloaded from.
Provide the name of the binary including the full URI.
Provide the IP address of the domain that hosts the binary.
There were 2 Suricata "A Network Trojan was detected" alerts. What were the source and destination IP addresses?
Taking a look at .top domain in HTTP requests, provide the name of the stealer (Trojan that gathers information from a system) involved in this packet capture using URLhaus Database.

Please, load the Infection3 packet capture in Brim to investigate the compromise event for the third machine.
Note: For questions that require multiple answers, please separate the answers with a comma.
Provide the IP address of the victim machine.
How many unique DNS queries were made to the domain associated from the first IP address from the previous answer?
How many binaries were downloaded from the above domain in total?
Provided the user-agent listed to download the binaries.
Provide the amount of DNS connections made in total for this packet capture.
With some OSINT skills, provide the name of the worm using the first domain you have managed to collect from Question 2. (Please use quotation marks for Google searches, don't use .ru in your search, and DO NOT interact with the domain directly).
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in