To access material, start machines and answer questions login.
Hidden Eye is a Modern Phishing Tool with Advanced Functionality And Multiple Tunneling Services {Android-Support-Available}. Supports over 34 pages to clone and phish. Also, supports key loggers.
********************
Clone the following github page:
Previous version link: https://github.com/DarkSecDevelopers/HiddenEye.gitUpdated link: https://gitlab.com/an0nud4y/HiddenEye
*********************
Enjoy the room and use it for educational/testing purposes ONLY.
*********************
Questions? Twitter: i7m4d
*********************
Special Thanks to MuirlandOracle for helping me polish this amazing room !
Check out his blog at https://muirlandoracle.co.uk/
cd to your preferred location
cd HiddenEye
sudo chmod +x HiddenEye.py
sudo pip3 install -r requirements.txt
sudo ./HiddenEye.py -f
It will ask to install LOCALTUNNEL, Enter N.
Please state Y to use this tool for educational/testing purposes ONLY.
Choose any site to clone.
Choose whether you want to add a key logger or not.
Choose to use CLOUDFLARE Protection
It optional whether you want the data to be emailed to you.
Enter a custom redirect link.
You can select any server to use.
Two links will be provided, copy the link and send it to your target.
{Educational Purposes Only}
After creating your phishing page, obviously you will not send the link provided by the tool as it is suspicious.
Go to https://bitly.com
Paste the url you copied and shorten it.
COPY THE NEW LINK & SEND IT TO YOUR TARGET.
{Use it ONLY for Educational Purposes.}
It is excellent to understand what a phishing page looks like to help secure yourself from leaking your credentials by accident.
In cyber-security the weakest link is humans.
A wise man said, to help secure yourself, is to understand how an attacker might approach to you.
This task will help you understand the difference between a legit/official page and phishing page even if it contains a HTTPS. Also, this task will help you create a Gmail phishing page.
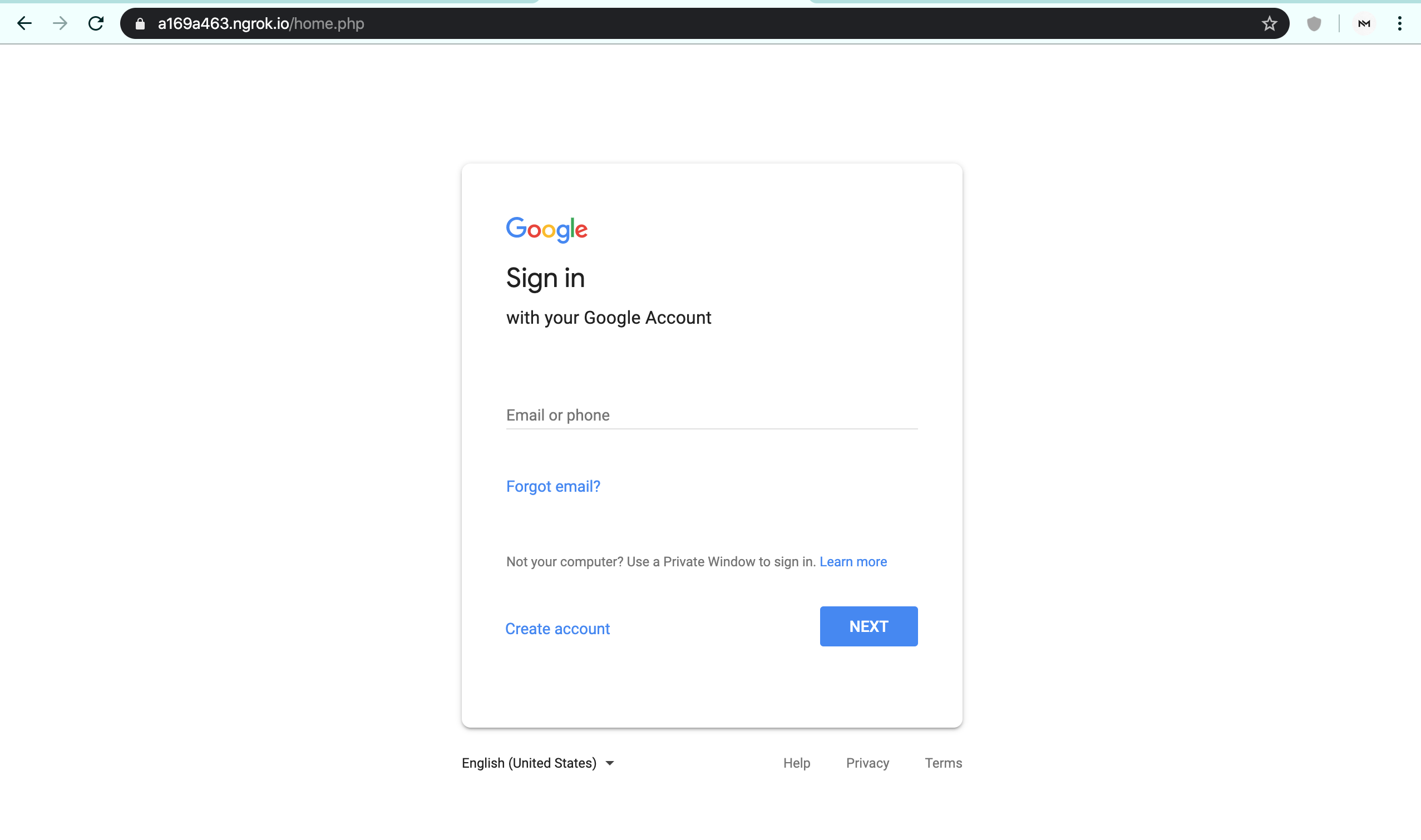
Image 1: Observe the content and URL of the page.
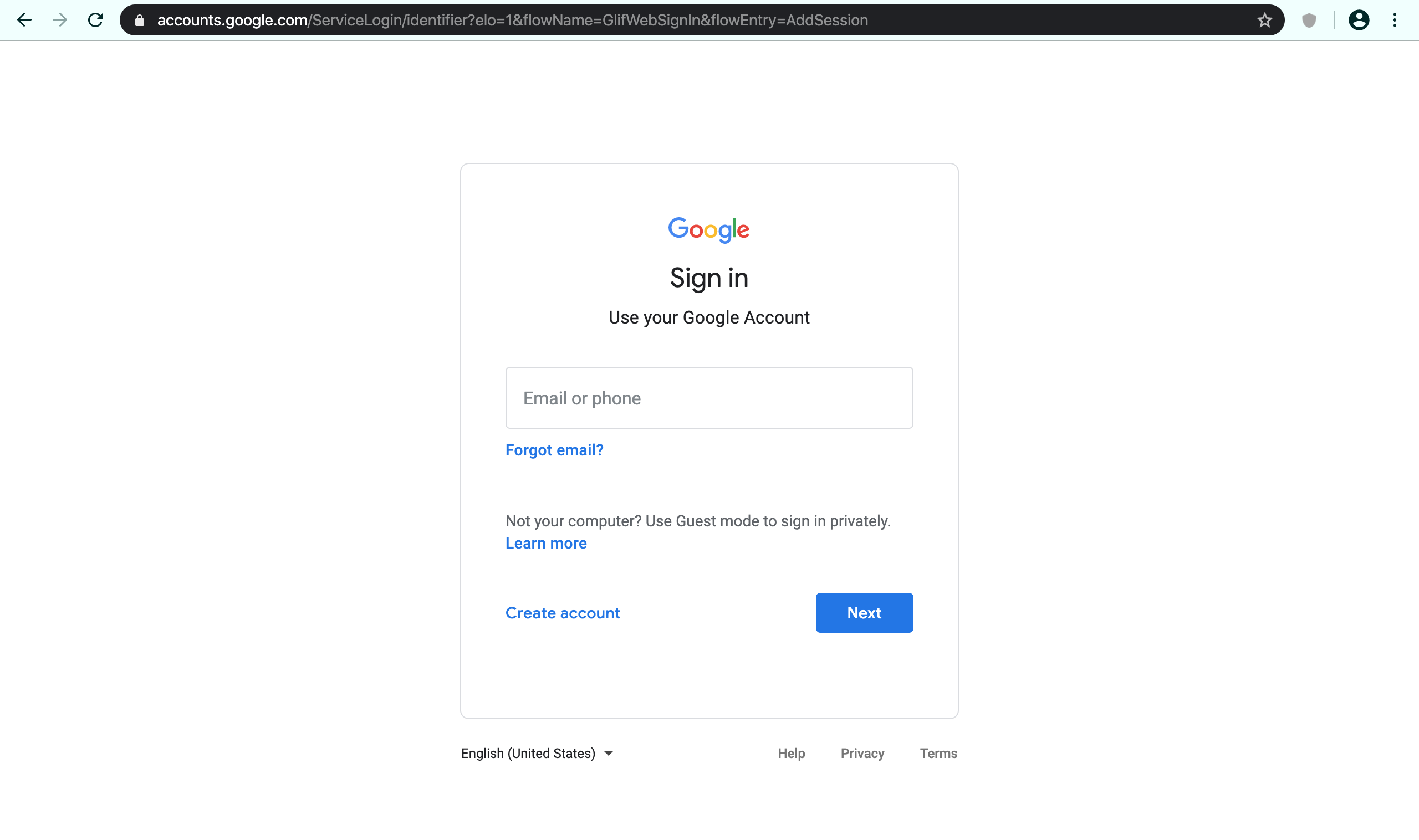
Image 2: Again, observe the content and URL of the page.
Which image shows a legit web-page? They are identical and most phishing pages nowadays have HTTPS enabled. (Image 1 or Image 2)
Similar to Task 1, lets try and make a Gmail phishing page.
And choose option 02, to create Gmail fake page.
Three options will be provided. Choose Standard Page Phishing.
As I explained in Task 1, the next options are optional.
Use option 1 Ngrok as a server.
Task 2, copy NGROK URL and mask it.
Send the masked link to the target.
I used a fake login details email: TryHackMeTest and Password: Test1 as an example just to show how it works.
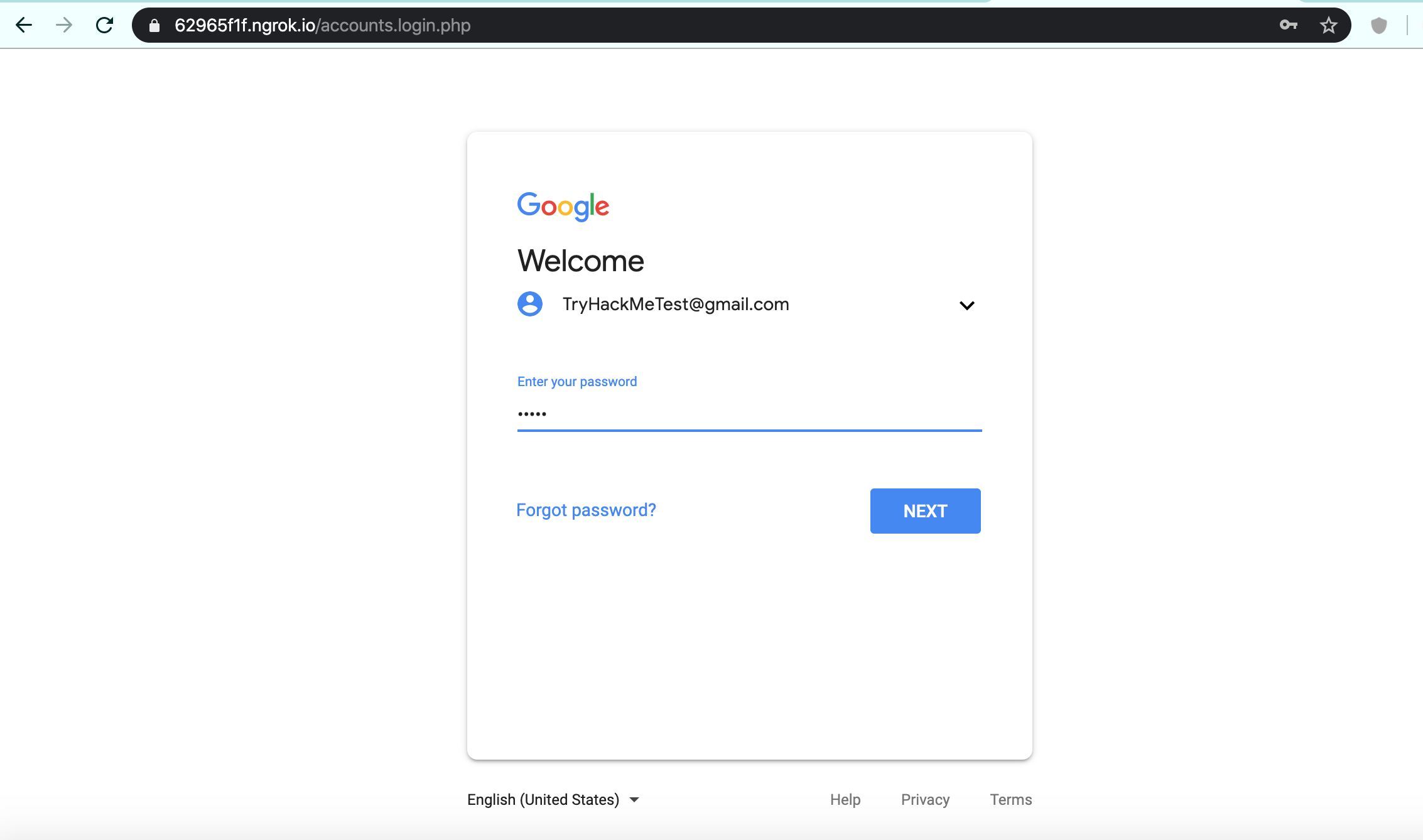
After the targets enters the login details and hit NEXT, the data will be visible to us in our terminal.
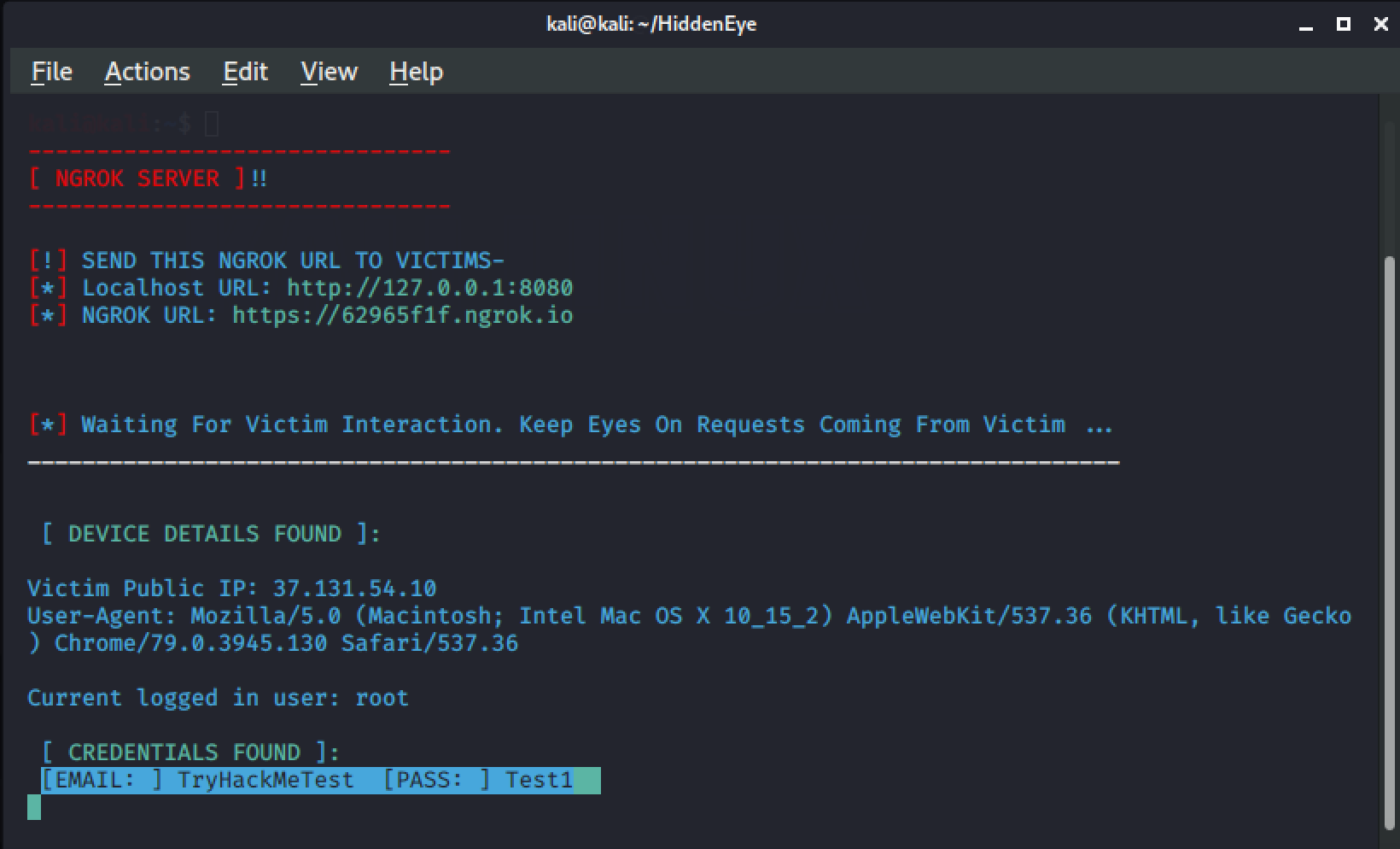
And thats all, we have got the target's login details !!!
What will you use this tool for?
What is the weakest link in cyber-security?
Do most phishing pages have HTTPS (Yay/Nay)?
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in

