To access material, start machines and answer questions login.

The Printer Exploitation Toolkit is a handy tool that is used for both local targeting and exploitation.
git clone https://github.com/RUB-NDS/PRET && cd PRET
python2 -m pip install colorama pysnmPpython pret.py will start an automatic printer discovery in your local network. 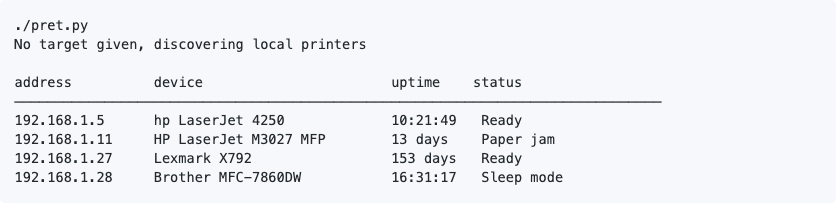
python pret.py {IP} pjl
python pret.py laserjet.lan ps
python pret.py /dev/usb/lp0 pcl help to see them.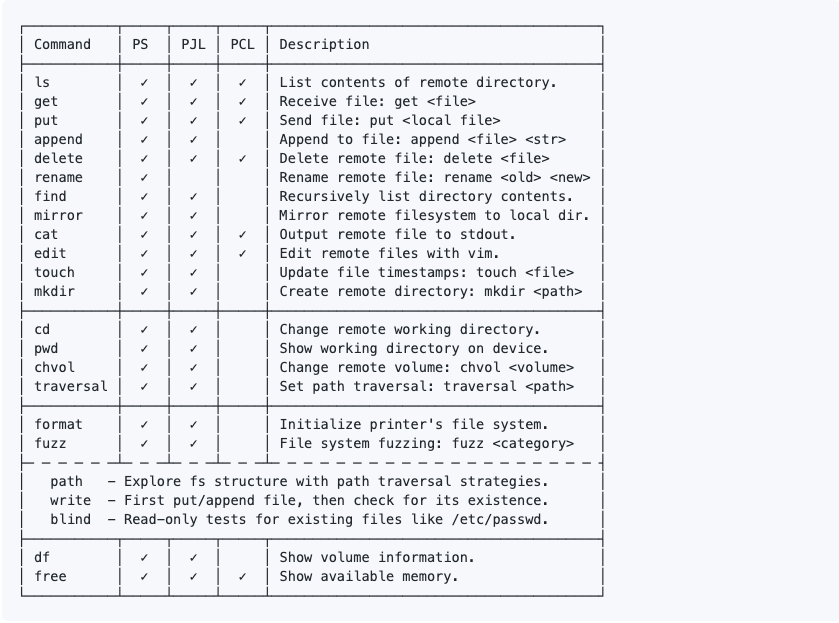
MACHINE_IP:631. See if you can retrieve any sensitive information. (PRET isn't going to work here as it is using port 9000 by default)
ssh printer@MACHINE_IP -T -L 3631:localhost:631Review the cheat sheet provided in the task reading above. What attack are printers often vulnerable to which involves sending more and more information until a pre-allocated buffer size is surpassed?
Connect to the printer per the instructions above. Where's the Fox_Printer located?
What is the size of a test sheet?
Turns out printer hacking isn't that hard at all. The problem here arises from low awareness of these issues and multiple misconfigurations made by administrators and users.

A small research project of mine suggested that it is possible to get almost full server file access by simply exploiting the printer service running on it. A shock from this discovery motivated me to create this room and bring more attention to this.
Now, make sure you secure your printer by making it invisible for the outer internet and re-configuring administrator access.
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in

