To access material, start machines and answer questions login.
A Security Operations Center (SOC) is a centralized security unit with team(s) responsible for protecting the organization against security threats.
A Security Operations Center Analyst, also known as a SOC Analyst, works in a SOC team to monitor, analyze, and respond to security issues as the front line of an organization's cyber defenses. Similarly, a Microsoft SOC Analyst has the same security goals as a SOC Analyst but with the additional distinction of working and specializing in Microsoft Security products.
The main goal is to reduce organizational risk. The mission statement would include the following points:
- Remediate active attacks in the environment.
- Advise on improvements to threat protection practices.
- Refer violations of organizational policies to appropriate stakeholders.
Responsibilities
| Monitoring | SOC Level 1 Analyst |
| Triage | SOC Level 1 Analyst |
| Incident Response | SOC Level 2 Analyst |
| Threat Hunting | SOC Level 2 Analyst |
| Advanced Threat Hunting | SOC Level 3 Analyst |
| Threat Intelligence (TI) Analysis | SOC Level 3 Analyst |
| Vulnerability Management | SOC Level 3 Analyst |
Prerequisites
- Understanding of Microsoft 365
- Fundamental understanding of Microsoft Security, Compliance, and Identity products
- Intermediate understanding of Microsoft Windows
- Familiarity with Azure services - specifically Azure SQL Database and Azure Storage, Azure VMs, and Virtual Networking
- Familiarity with scripting concepts
This role primarily investigates, responds to, and hunts for threats by using the following security products:
- Microsoft Sentinel
- Microsoft Defender for Cloud
- Microsoft 365 Defender
- and third-party security products
Throughout the Microsoft Sentinel module, we will dive deep into these security products and learn how they help SOC Analysts with their job tasks. Keeping this role definition in mind, let's see what Microsoft Sentinel is in the next task.
Generally, which level of SOC Analyst is responsible for responding to incidents?
Besides monitoring, what else do SOC Level 1 Analysts spend the majority of their time with?
Before we can define what Microsoft Sentinel is, it is important to first define two concepts, namely SIEM and SOAR.
What Is SIEM?
SIEM stands for Security Information and Event Management. It is a comprehensive approach to security management that combines Security Information Management (SIM) and Security Event Management (SEM) into a single solution. The primary purpose of SIEM is to provide a holistic view of an organization's information security by collecting and analyzing log data from various sources across its IT infrastructure.
What Is SOAR?
SOAR stands for Security Orchestration, Automation, and Response. It is a set of technologies and practices designed to improve the efficiency and effectiveness of an organization's cyber security operations. SOAR platforms integrate security orchestration and automation to streamline and accelerate incident response processes.
What Is Microsoft Sentinel?
Given the above concept definitions, Microsoft Sentinel's own definition becomes a combination of the two. It is essentially a scalable, cloud-native solution that provides the following:
- Security Information and Event Management (SIEM) functionality by:
- Collecting and querying logs
- Doing correlation or anomaly detection
- Creating alerts and incidents based on findings
- Security Orchestration, Automation, and Response (SOAR) functionality by:
- Defining playbooks
- Automating threat responses
Microsoft Sentinel also delivers security analytics and threat intelligence across the organization. It's a one-stop-shop and bird's-eye view solution for:
- Attack detection
- Threat visibility
- Proactive hunting
- Threat response
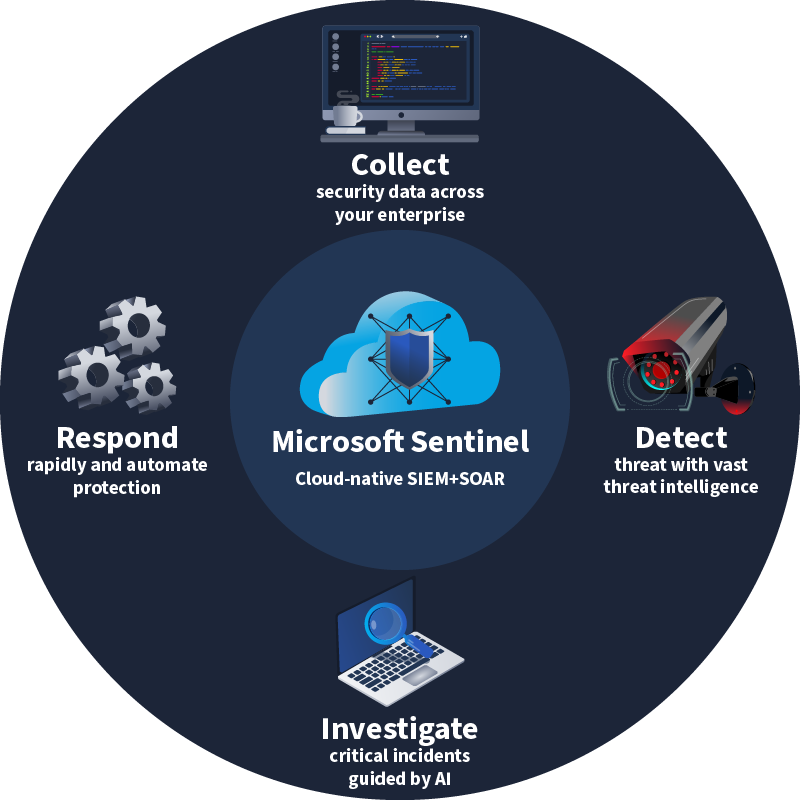
Microsoft Sentinel performs the above actions and enables security operations by means of 4 main pillars:
- Collect
- Detect
- Investigate
- Respond
As we go through the rooms in this module, it will be clear which functionalities are SIEM and which ones are SOAR-related. For now, we can think of Microsoft Sentinel as a cloud-native SIEM+SOAR system for security operations.
Creating security alerts and incidents is part of which security concept?
By means of how many pillars does Microsoft Sentinel help us to perform security operations?
To understand how Microsoft Sentinel does what it does, maybe it is better to go through the journey together with the logs. Without log data ingested from different data sources, there wouldn't be any correlation, alerting, threat intelligence, or response automation.
Phase 1: Collect
- Data connectors: The first step is to ingest data into Microsoft Sentinel. This is exactly what data connectors are for. There are 100+ connectors to cover all various data sources and scenarios.
- Log retention: Once the data has been ingested into Microsoft Sentinel, it must be stored for further correlation and analysis. This log storage mechanism is called Log Analytics workspaces. Data stored in these workspaces can be queried to gain further insights using Kusto Query Language (KQL).
Phase 2: Detect

- Workbooks: Workbooks are essentially dashboards in Microsoft Sentinel used to visualize data. There are many built-in workbooks, and custom ones can also be created by utilizing KQL.
- Analytics rules: What good is a bunch of logs and visualizations if we can't gain insights from them? That's why there are Analytics rules. Analytics rules provide proactive analytics so that SOC teams get notified when suspicious things happen. The output of running Analytics rules are security alerts and incidents.
- Threat hunting: Reacting to security incidents only after they happen is not good enough. SOC analysts also need to perform proactive threat hunting. Microsoft Sentinel has over 200 built-in threat-hunting queries to support that needle-in-a-haystack job.
Phase 3: Investigate
- Incidents and investigations: Once Analytics rules detect suspicious activities, i.e., once an alert is triggered, security incidents are created for SOC analysts to triage and investigate. Typical incident management activities include:
- Changing the incident status
- Assigning to other analysts for further investigation
- Mapping entities to the investigation
- Investigating the incident timeline
- Deep-dive into investigation details using investigation maps
- Recording investigation comments
Phase 4: Respond
Let's first define the term alert fatigue. Alert fatigue occurs occurs when cyber security professionals are inundated with a high volume of security alerts, which leads to a diminished ability for SOC teams to react effectively to and investigate real threats.
- Automation via playbooks: One of the main challenges of a SOC team is alert fatigue. To overcome alert fatigue, automation in security operations is a must. This is done by automated workflows, also known as playbooks, in response to events. By doing so, automated responses can be provided for:
- Incident management
- Enrichment
- Investigation
- Remediation
Referring to the definition of SOAR in Task 2, Respond is part of the SOAR (Security Orchestration, Automation, and Response) capabilities of Microsoft Sentinel.
After defining the four phases above (Collect, Detect, Investigate, and Respond), it should be clearer how Microsoft Sentinel helps SOC analysts perform their job tasks and which of these phases map to L1/L2 SOC analyst's responsibilities.
Where are the ingested logs stored for further correlation and analysis?
Workbooks are essentially _______ used for visualization.
When SOC teams are flooded with security alerts and incidents, this is called?
In Microsoft Sentinel, automation is done via automated workflows, known as?
The output of running Analytics rules includes security alerts and?
With Microsoft Sentinel, there is no need for server provisioning. This means it is?
In this room, we have delved into an initial introduction to security operations as a whole, understanding the responsibilities of a SOC Analyst and some key prerequisites.
We also discussed some key concepts of Microsoft Sentinel, how it works, and how SOC Analysts can use it to improve their security posture.
After completing this Microsoft Sentinel introductory room, you should have learnt the following:
- The roles of a SOC Analyst and the different levels
- How Microsoft Sentinel works as a SIEM solution
- The key features of Microsoft Sentinel
I understand how Microsoft Sentinel works!
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in


