To access material, start machines and answer questions login.
Why TShark?
Bored with trying to extract packets by hand? Need to get info from a pcap file that doesn't extract easily from Wireshark? Are GUIs for losers but now you realized you can't open Wireshark? Well my friend, TShark is the solution to all your problems.
Installation
Before beginning, we need to make sure we have tshark installed on our host - If you are using the AttackBox you can skip this, as it already has tshark installed.
Generally, tshark is installed with Wireshark. But let's verify it's installed anyway. Run the command below to determine if it's installed or not.
apt list tshark
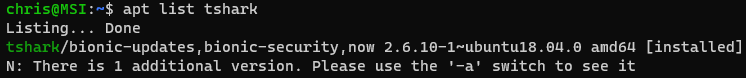
In my output above, we can see that it is installed. If it's not installed, sudo apt install tshark will do the trick.
The tshark program is also available in a Windows installation as tshark.exe in the Wireshark install directory.
Try running tshark -h to get the help output to make sure we can access the program properly.
Mark complete once installed/verified
This task uses the dns.cap capture file on the Wireshark SampleCaptures wiki page.
To read a file with TShark, we will use the -r switch. This will display a summary line of each packet similar to tcpdump output and is useful to identify high-level information about the capture.
tshark -r dns.cap
When paired with wc -l, we can quickly identify how many packets are in a capture.
tshark -r dns.cap | wc -l
We can utilize Wireshark display filters (which are DIFFERENT than bpf syntax) to narrow down what packets are displayed. If we're interested in DNS A records only, we can use the dns.qry.type == 1 display filter to narrow down our packets. Display filters are added using the -Y switch. Our command below will show all of the A records in our capture, including responses.
tshark -r dns.cap -Y "dns.qry.type == 1"
The power of TShark comes with combining traditional Wireshark filters with extraction. We can extract specific field values directly from the pcap, allowing us to have only the interesting fields returned. One way to extract data is using the -T fields and -e [fieldname] switches. To extract the A records in the pcap, we would use -T fields -e dns.qry.name at the end of our previous tshark command. This makes our command the one below:
tshark -r dns.cap -Y "dns.qry.type == 1" -T fields -e dns.qry.name
NOTE: An easy way to identify field names in Wireshark is to navigate to the Packet Details in the capture, highlight the interesting field, then view the bottom left corner.
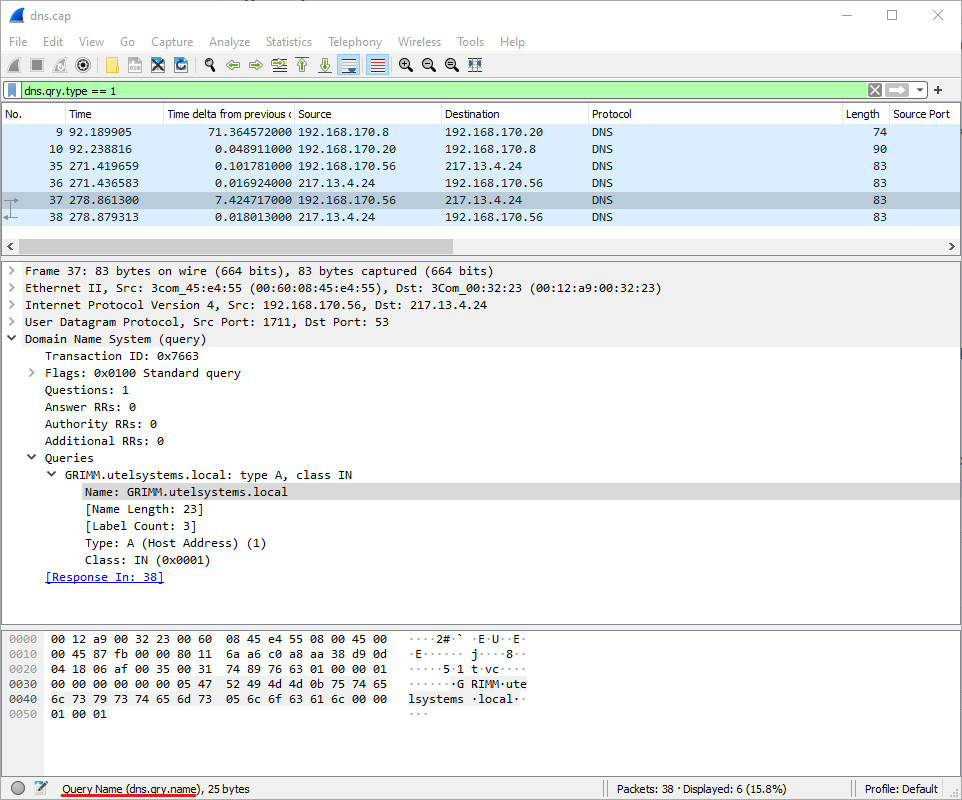
How many A records are in the capture? (Including responses)
Which A record was present the most?
We've been alerted that a host in our network has been exfiltrating data over DNS, can you find it?
Use the attached file to analyze in Wireshark and TShark to find the exfiltrated data. As you identify suspicious items in Wireshark, pivot to TShark to extract relevant information.
Remember, we can filter out irrelevant packets with the -Y switch using display filters.
How many packets are in this capture?
How many DNS queries are in this pcap? (Not responses!)
What is the string extracted from the DNS queries?
What is the flag?
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in
