To access material, start machines and answer questions login.
Which ports are open? (in numerical order)
What programming language is the backend written in?
Now that you know what's running, you need to investigate. With webapps, the normal process is to click around. Create an account, use the web app as a user would and play close attention to details.
Create your own user account
Log in to your account
Try and log in to an invalid user account
Try and log in to your account, with an incorrect password.
Notice the timing difference. This allows user enumeration
Use the timing attack
Now that we know there's a timing attack, we can write a python script to exploit it.
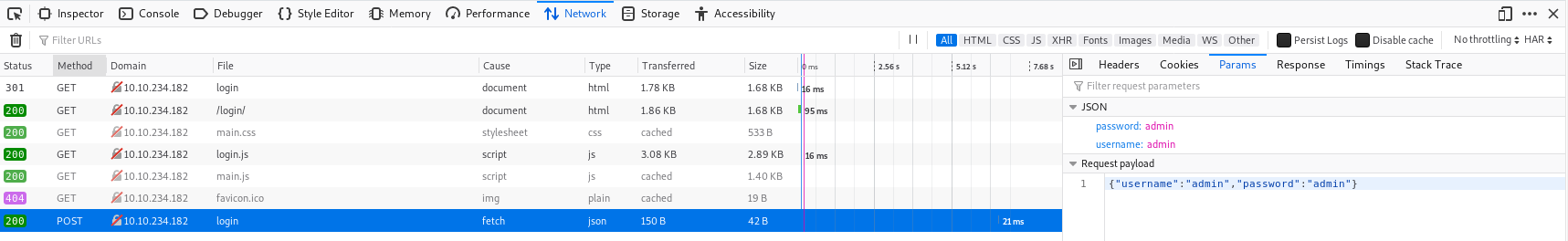
The first step is working out how login requests work. You can use Burpsuite for this, but I prefer to use Firefox dev tools as I don't have to configure any proxies.
Here we can see the login is a POST request to /api/user/login. This means we can make this request using CURL, python or another programming language of your choice.
In python, we can use this code and the Requests library to send this request as follows:
creds = {"username":username,"password":"invalidPassword!"}
response = r.post(URL,json=creds)The next stage is timing this. Using the "time" standard library, we can work out the time difference between when we send the request and when we get a response. I've moved the login request into it's own function called doLogin.
startTime = time.time() doLogin(user) endTime = time.time()
The next step is now to repeat this for all usernames in the username list. This can be done with a series of for loops. The first will read usernames from a file into a list, and the second will test each of these usernames and see the time taken to respond. For my exploit, I decided that times within 10% of the largest time were likely to be valid usernames.
Why does the time taken change?
The backend is intentionally poorly written. The server will only try to verify the password of the user if it receives a correct username. The psuedocode to explain this better is below.
def login(username, password):
if username in users: ##If it's a valid username
login_status = check_password(password) ##This takes a noticeable amount of time
if login_status:
return new_session_token()
else:
return "Username or password incorrect"
else:
return "Username or password incorrect"
Pre-written exploits in Golang and Python are available here: https://github.com/NinjaJc01/hackerNoteExploits
Use the Honeypot capture or Names/names.txt from https://github.com/danielmiessler/SecLists/tree/master/Usernames. The shorter the list is, the faster the exploit will complete. (Hint: one of those wordlists is shorter.)
NOTE: The Golang exploit is not reliable but it is faster. If you get invalid usernames, try re-running it after a minute or switching to the python exploit.
Try to write a script to perform a timing attack.
What are/is the valid username(s)?
Next Step
Now that we have a username, we need a password. Because the passwords are hashed with bcrypt and take a noticeable time to verify, bruteforcing with a large wordlist like rockyou is not feasible.
Fortunately, this webapp has password hints!
With the username that we found in the last step, we can retrieve the password hint. From this password hint, we can create a wordlist and (more) efficiently bruteforce the user's password.
Create your wordlist
The password hint is "my favourite colour and my favourite number", so we can get a wordlist of colours and a wordlist of digits and combine them using Hashcat Util's Combinator which will give us every combination of the two wordlists. Using this wordlist, we can then use Hydra to attack the login API route and find the password for the user. Download the attached wordlist files, look at them then combine them using hashcat-util's combinator.
Hashcat utils can be downloaded from: https://github.com/hashcat/hashcat-utils/releases
Either add these to your PATH, or run them from the folder.
We want to use the Combinator.bin binary, with colors.txt and numbers.txt as the input. The command for this is (assuming you're in the directory with the binaries and have copiesd the txt files into that directory):
./combinator.bin colors.txt numbers.txt > wordlist.txt
This will then give you a wordlist to use for Hydra.
Attack the API
The HTTP POST request that we captured earlier tells us enough about the API that we can use Hydra to attack it.
The API is actually designed to either accept Form data, or JSON data. The frontend sends JSON data as a POST request, so we will use this. Hydra allows attacking HTTP POST requests, with the HTTP-POST module. To use this, we need:
- Request Body - JSON
{"username":"admin","password":"admin"} - Request Path -
/api/user/login - Error message for incorrect logins -
"Invalid Username Or Password"
The command for this is (replace the parts with angle brackets, you will need to escape special characters):
hydra -l <username> -P <wordlist> 192.168.2.62 http-post-form <path>:<body>:<fail_message>
Form the hydra command to attack the login API route
How many passwords were in your wordlist?
What was the user's password?
What's the user's SSH password?
Log in as the user to SSH with the credentials you have.
What's the user flag?
Enumeration of privileges
Now that you have an SSH session, you can grab the user flag. But that shouldn't be enough for you, you need root.
A good first step for privilege escalation is seeing if you can run sudo. You have the password for the current user, so you can run the command:
sudo -l
This command tells you what commands you can run as the superuser with sudo. Unfortunately, the current user cannot run any commands as root. You may have noticed, however, that when you enter your password you see asterisks. This is not default behaviour. There was a recent CVE released that affects this configuration. The setting is called pwdfeedback.
What is the CVE number for the exploit?
Find the exploit from https://github.com/saleemrashid/ and download the files.
Compile the exploit from Kali linux.
SCP the exploit binary to the box.
Run the exploit, get root.
What is the root flag?
Web app
This room was designed to be more realistic and less CTF focused. The logic behind the timing attack is mentioned in OWASP's authentication section, and a fairly similar timing attack existed on OpenSSH, allowing username enumeration. I've included links to this in the Further Reading section
Password hints in webapps are normally considered bad practice, but large companies still often include them. Adobe suffered a large databreach affecting users of Creative Cloud and decryption of the passwords was made much easier due to the password hints also included in the breach.
Privilege Escalation
The privilege escalation for this box is a real world CVE vulnerability, and affected the default configurations of sudo on macOS, Linux Mint and ElementaryOS.
Further reading
Timing attacks on logins
https://seclists.org/fulldisclosure/2016/Jul/51
https://www.gnucitizen.org/blog/username-enumeration-vulnerabilities/
https://wiki.owasp.org/index.php/Testing_for_User_Enumeration_and_Guessable_User_Account_(OWASP-AT-002)
Adobe Password Breach
https://nakedsecurity.sophos.com/2013/11/04/anatomy-of-a-password-disaster-adobes-giant-sized-cryptographic-blunder/
Sudo CVE
https://dylankatz.com/Analysis-of-CVE-2019-18634/
https://nvd.nist.gov/vuln/detail/CVE-2019-18634
https://tryhackme.com/room/sudovulnsbof
Read, explore, learn.
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in

