To access material, start machines and answer questions login.
What are the basic principles of Digital Forensics and Incident Response (DFIR), and why are they crucial? How do ethical considerations impact digital investigations, and what role does the Chain of Custody play in managing digital evidence? What best practices should be followed to analyze digital evidence while complying with legal and regulatory standards?
In this room, we will explore the foundational principles of Digital Forensics and Incident Response (DFIR), ethical considerations in digital investigations, the importance of the Chain of Custody in digital evidence management, the legal standards for acquiring and handling forensic disk images, and best practices for analysing digital evidence in compliance with legal and regulatory standards.
Learning Objectives
The following topics are tailored to equip DFIR Teams, Legal Advisors, and Compliance Officers with the necessary knowledge to navigate the complexities of legalities in digital investigations:
- Understanding the foundational principles of DFIR.
- Recognising the ethical considerations in digital investigations.
- Learning about legal compliance and evidence handling in DFIR.
- Understanding the importance of the Chain of Custody in digital evidence management and its legal implications.
- Learning the legal standards for acquiring and handling forensic disk images to ensure admissibility in court.
- Examining best practices for analysing digital evidence while complying with legal and regulatory standards.
Room Prerequisites
Embark on this comprehensive module designed to enhance your proficiency in swiftly recognising security breaches and assessing their magnitude, reinforcing the legal integrity of DFIR practices across various platforms.
Connecting to the machine
Let's start the virtual machine in a split-screen view by clicking the green Start Machine button on the upper right section of this task. If the VM is not visible, use the blue Show Split View button at the top-right of the page. Alternatively, using the credentials below, you can connect to the VM via RDP. Please allow the machine at least 4 minutes to fully deploy before interacting with it.

| Username | analyst |
| Password | DFIR321! |
| IP | MACHINE_IP |
IMPORTANT: The VM has all the artefacts and clues to understand the underlying incident and legal considerations. There is no need for fancy hacks, brute force, and the like. Dive into the simulated corporate scenario and start the detective work! Microsoft Outlook will start on its own. Kindly ignore the activation key window by pressing Back, and then proceed by clicking Skip for now ⇒ Use as view only. When asked for a license, click X; for optional data, click Next ⇒ Don't send optional data ⇒ Done in the subsequent pop-up windows.
Disclaimer
This fictional scenario presents a narrative with invented names, characters, and events. It is not meant to suggest any connection or resemblance to actual individuals, locations, structures, or merchandise. The screenshots of Microsoft Edge and the Excel below are only examples for illustration purposes and do not require interaction.
Incident Scenario
The Chief Finance Officer (CFO) received an email receipt for an unauthorised transaction of over $9,000.00. Despite the billing information implicating the CFO and their Executive Assistant (EA), they both vehemently deny making the purchase. The CFO promptly alerted the Human Resources (HR) and Security Operations (SecOps) team to investigate the matter. As a member of the SecOps team, you and your team were tasked to investigate the matter and identify whether a security breach had occurred.
IMPORTANT: The questions have been tailored to focus only on relevant artefacts to the incident. We will apply the concepts covered within each task concerning the incident as we walk through it from the lens of an incident responder.
Incident Detection and Initial Response
Incident detection doesn't depend just on purely technical controls but also on the active involvement and contribution of the individuals affected. For incident responders to recognise, acknowledge, and declare an incident, whether related to security or operations, they must remain calm, understand the situation, and consider these varied sources of information.
The initial response to an incident can be shaped by various factors, including the incident's nature, available information, and the incident responder's experience. In our example above, the response typically involves piecing together indirect evidence and leveraging different investigative techniques and tools to address the incident comprehensively.
Importance of Documentation
Proper documentation is critical in detailing what happened during an incident. Key points to document include:
- Details on the person (or persons) of interest (POI), someone being investigated or questioned, and their involvement in the incident.
- The specific actions that led to the incident, such as entering sensitive information into a suspected phishing site.
- Nature and extent of the data compromised or lost.
- Any direct or indirect evidence that will help shed light on the incident.
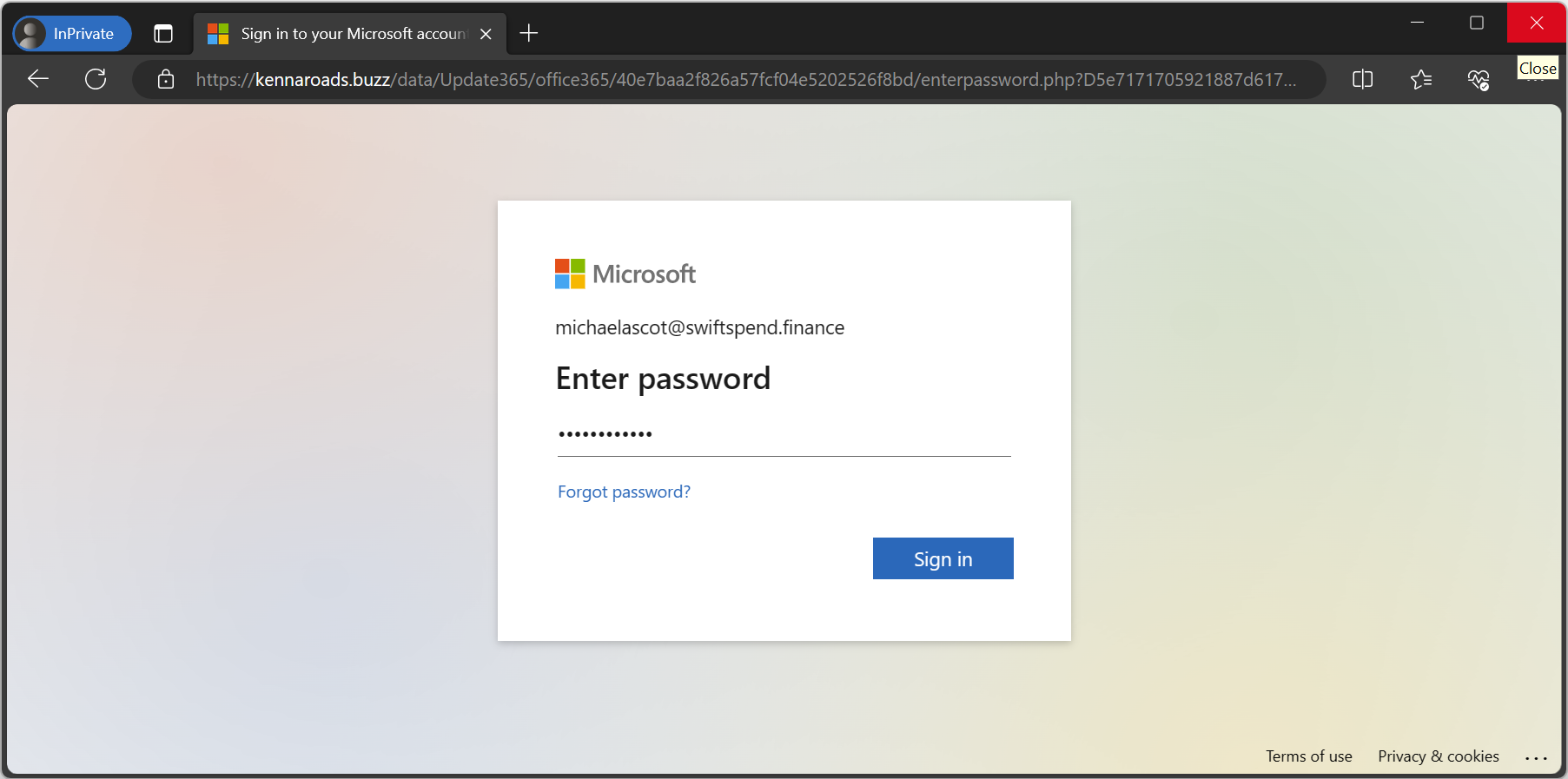
In our example scenario, even if the browsing history of a given machine was not present, it does not negate the machine's interaction with the phishing site or the occurrence of the phishing itself. Acknowledging the principle that Absence of Evidence is not Evidence of Absence may help show the need to look at other sources of information. Other indicators, like network logs or unusual account activity, may still reveal the incident's traces, highlighting the importance of investigating beyond apparent sources.
Pinpointing when it happened is just as crucial. Important timestamps to record are:
- The exact time and date the incident was detected and believed to have occurred. This should ideally be logged in a standard format such as UTC to ensure it can be matched to other sources.
- Timeline of events leading up to the detection.
- Response times and actions are taken immediately following detection.
Understanding why it happened and how to prevent it from happening again are fundamental to strengthening future security. Essential points include:
- Analysing the cause (e.g., Assessing how the phishing scam was successful and the vulnerabilities exploited, if any).
- Identifying and documenting gaps in knowledge, communication, or technical defences that the incident highlighted.
- Formulating recommendations for policy updates, training enhancements, and technical measures to prevent recurrence.
The value of thorough documentation lies not only in enhancing organisational transparency but also in ensuring court admissibility. Precisely recording repeatable steps in incident response strengthens the legal standing of the actions undertaken and the evidence presented.
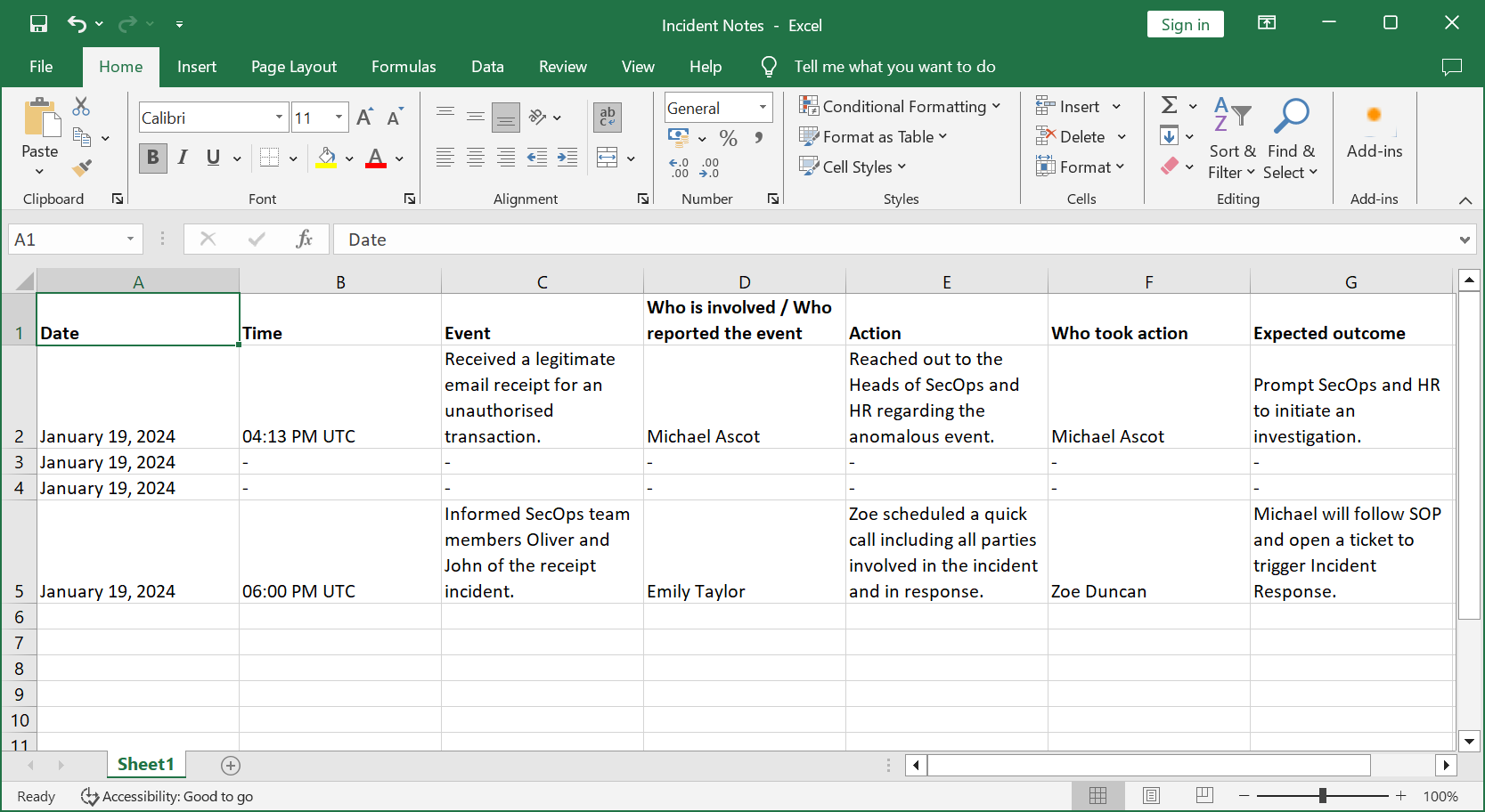
While one may conduct the finest analysis and possess the most compelling evidence, its value is nullified if it can't be presented in court. Thorough documentation ensures these critical insights are admissible and impactful when and where they matter most.
Standard Operating Procedures for Communicating an Incident
Establishing well-defined communication protocols before and during the early stages of an incident is vital. These protocols serve as a guide to ensure:

|
|
Having predefined channels and templates for communication can significantly reduce decision fatigue and response time during a high-pressure incident.
The importance of an Incident Response (IR) Process to handle potential detection and response capability gaps due to a lack of communication and awareness cannot be overstated. A robust IR Process:
- Establishes a Clear Reporting Path: Constituents are well-informed about the process to follow when they feel or think something is off, ensuring concerns are addressed promptly and effectively.
- Defines Roles and Responsibilities: Each member of the IR team knows their tasks and how to communicate their progress to key stakeholders.
- Ensures Continual Updates: Regular updates are crucial for adapting strategies as the situation evolves and keeping all parties informed.
- Facilitates Post-Incident Review: Effective communication before, during and after an incident contributes to a more efficient review process, identifying lessons learned and areas for improvement.
A structured communication approach is essential for bridging detection and response capabilities gaps, often caused by misunderstandings or lack of information.
Moreover, having a well-defined communication protocol and a robust IR Process is beneficial and necessary for effective incident management. These ensure that all involved parties are coordinated, informed, and prepared to respond promptly and effectively, thereby mitigating the impact of the incident and paving the way for a swift recovery.
Reminder: Proceed with the tasks with the mindset of an incident responder, your assigned role. Focus on advancing the investigation by following established procedures and utilising your investigative skills. Your decisions and actions should align with the scenario and its objectives. Now, let's proceed with the investigation.
What is the Ticket# of the reported incident?
What is the email of the primary person of interest (POI)?
Who is the POI reporting to?
What specific kind of logs was requested from IT?
What is the timestamp of IT's response to the request for logs?
Evidence-based Approach
A digital forensics practitioner must refrain from hastily making conclusions and judgment calls. For instance, viewing a person of interest from a judgemental lens of suspicion may be construed as personal bias, which should not be allowed to cloud the results of an investigation.
Using evidence properly is critical to ensuring investigations are thorough and follow the law. Focusing on what the evidence shows makes it hard to argue against facts and enables an investigation to yield conclusive results that strictly adhere to legal requirements. Additionally, this approach is repeatable, meaning that others following the same methods should arrive at similar, if not the same, conclusions, further strengthening the investigation's integrity.
Burden of Proof in Digital Forensics
Investigators need to provide sufficient and credible evidence to support their findings. This principle ensures that conclusions are not based on assumptions or incomplete information.
The burden of proof demands adherence to a high standard of evidence, ensuring that the conclusions drawn are not only supported by the evidence but are also legally defensible. It serves as a reminder that the investigator is responsible for building a case that withstands scrutiny, adhering to legal standards and ethical guidelines throughout the investigative process.
Ethical Decision-Making in Digital Investigations
|
Making ethical decisions is imperative during investigations as it helps prevent practitioners from doing something wrong or illegal while trying to find the truth. Understanding and applying these principles is vital for any professional in the field, ensuring that their work is influential, respected, and legally sound. It is crucial to consider ethics, especially when dealing with people's privacy and the needs of an investigation. Ethics in this field means being authorised to perform specific actions such as collecting, preserving, and analysing electronic information while ensuring the privilege granted is not abused beyond its purpose. Ensuring these actions are only performed during the investigation to uncover the truth — no more, no less. A noteworthy ethical issue is privacy. Sometimes, investigators might see personal and sensitive information during their investigation, which can be problematic if they use it outside the scope of their work. Dealing with these issues is about honesty, respecting privacy, and following strong moral principles. |

|
Legal Compliance in Digital Forensics
Legal compliance is a fundamental aspect of digital forensics. A multitude of legal frameworks and privacy laws govern digital investigations, including the Sarbanes-Oxley Act of 2002 (SOX), devised to combat fraudulent accounting and financial practices that have substantial implications for security and data retention, and the Computer Fraud and Abuse Act of 1986 (CFAA), which outlines illegal digital activity.
For instance, the SOX Act, post-Enron scandal, significantly impacts how corporate data is managed and audited, presenting a complex landscape for investigators. Similarly, the CFAA, often debated for its broad interpretations, has led to notable cases like United States v. Lori Drew, highlighting the intricate interplay between ethical discernment and legal mandates in digital investigations.
These case studies and laws also show the necessity of an evidence-based approach, where every action and decision in a digital investigation is grounded in legality and ethical integrity. It's not just about finding the truth but doing so in a manner that respects individual rights and adheres to the legal framework, thus ensuring that the outcomes of investigations are both valid and defensible in a Court of Law.
It is crucial to differentiate DFIR work from a security or maturity assessment that evaluates compliance with frameworks like PCI-DSS. Our objective is not to pinpoint vulnerabilities. Our focus in DFIR is akin to piecing a puzzle together, where evidence is gathered and collected by acquiring and analysing artefacts to uncover the truth.
Consider a case where a financial institution faces unauthorised data access. Our task as DFIR professionals is like puzzle-solving: we methodically gather and analyse pieces of digital evidence - tracing digital footprints, reviewing access logs, and recovering deleted files.
This process is not about assessing implementation compliance with standards like PCI-DSS but following a systematic, evidence-based approach. We aim to see and construct a clear picture of the incident from a broader perspective, ensuring our findings are factual, based on solid evidence, and can be replicated to reach the same conclusions.
Responsibility of Authority in Digital Investigations

|
Authority figures in digital investigations, including incident responders, investigators, and law enforcement officials, bear significant responsibility. They play a crucial role in ensuring the integrity and effectiveness of digital forensic investigations by ensuring that investigations comply with legal standards while upholding ethical integrity. Their role involves:
Additionally, authorities are responsible for fostering a culture of ethical decision-making and transparency. They must train and mentor their teams, emphasising the importance of lawful and justifiable actions in investigations. Keeping abreast of evolving legal standards and technological advancements is also essential to their role, ensuring that their teams are well-equipped for thorough and compliant investigations. |
Understanding Authority in Digital Investigations
People have different views on ethics and law, but those in charge, like judges and district attorneys, make the final decisions when it comes to legal matters. It shows the importance of recognising and respecting the people who have the power to enforce and interpret the law.
Laws like the SOX Act and CFAA can be interpreted differently in different places or by other judges. But in the end, judges, lawmakers, and law enforcement officials have the final word. Recognising authority means understanding who is in charge and accepting that they have the final say, even if you might have your own opinions.
As an incident responder, it's also crucial for those under investigation to recognise your authority. Your role is to follow the legal system's structure and ensure investigations meet the higher legal and ethical standards. Staying up-to-date with how laws are interpreted and changing is part of this. Balancing personal ethics, professional behaviour, and following legal rules is critical to doing good work in digital investigations.
Based on email communications, what clause of the Acceptable Use Policy (AUP) email received by the POI did they violate?
What is the User-Agent of the anomalous IP address with a successful login attempt?
Rules of Court in Various Jurisdictions

|
Rules of Court are essential guidelines that direct how legal proceedings are conducted in different places. While each country or jurisdiction might have its own specific rules, there are common principles that courts everywhere follow. These include things like how trials are structured, the roles of judges and lawyers, and how evidence is presented. These rules ensure that legal cases are handled and organised. They help keep court proceedings clear and systematic, ensuring everyone understands the process. Additionally, these rules protect the rights of all parties in a trial, from the accused to the victims. Maintaining these rules is crucial for the justice system. Judges, lawyers, and other legal professionals must follow them closely to guarantee that justice is served correctly and fairly for everyone. |
Rules of Evidence in Various Jurisdictions
The Rules of Evidence are foundational principles that govern the admissibility, relevance, and quality of evidence in legal proceedings across various jurisdictions. While specific rules vary per country or jurisdiction, core concepts are universally recognised worldwide in courtrooms.
Key among these is the principle of relevance, ensuring that all evidence presented is directly related to the case at hand. Additionally, evidence must be reliable and believable, which requires checking and confirming its authenticity.
These rules serve the dual purpose of safeguarding the legal process and ensuring fair proceedings. Authorities in legal and investigative fields, including judges and attorneys, are responsible for upholding these rules and applying them judiciously to ensure justice while honouring the rights of every individual involved.
Chain of Custody and Handling Digital Evidence
Often, court rules typically do not allow hearsay or indirect information, except in exceptional cases. Hence, keeping evidence safe from tampering or damage is essential.
The Chain of Custody records who handled the evidence and how it was protected, from when it was collected until it was presented in court, ensuring the evidence is genuine and unchanged. The general process is as follows:
|

|
Court Admissibility of Evidence
For digital evidence to be admissible in court, it must be relevant, reliable, and obtained legally. The Chain of Custody plays a pivotal role in demonstrating these aspects by providing a transparent and traceable link from the evidence to the matter at hand. Proper procedures and adherence to established forensic standards are paramount in maintaining the integrity and admissibility of the evidence.

Adhering to these guidelines and procedures ensures digital evidence is handled with the utmost care and professionalism, maintaining its integrity and standing in legal contexts. As a result, it supports the pursuit of justice, ensuring that the truth is accurately represented and upheld in legal proceedings.
Who took the SHA1 hashes of the IIS log files of the Exchange Server?
What is the SHA1 hash of the Offline Storage Table (OST) file from the POI's device?
Congratulations! You've completed the Legal Considerations for DFIR room.
In summary, we were able to learn and perform the following:
- Understanding the foundational principles of DFIR.
- Recognising the ethical considerations in digital investigations.
- Learning about legal compliance and evidence handling in DFIR.
- Understanding the importance of the Chain of Custody in digital evidence management and its legal implications.
- Learning the legal standards for acquiring and handling forensic disk images to ensure admissibility in court.
- Examining best practices for analysing digital evidence while complying with legal and regulatory standards.
If you enjoyed this room, continue learning and developing proficiency in areas specific to Security Operations, Digital Forensics, and Incident Response tooling, which may enhance your overall Blue Teaming skills:

|
|
Recognising that these security tools truly flourish in the hands of skilled individuals with the necessary information and technical expertise to combat potential threats and manage security incidents is vital.
Next Steps
As we conclude, we hope this room has instilled in you the necessary knowledge about Legal Considerations for DFIR. It is now time to proceed to the next room, IR Playbooks. May you harness this knowledge to fortify defences, identify adversaries, and drive your cyber security endeavours forward.
If you liked this room, the Digital Forensics Case B4DM755 room is an excellent challenge demonstrating the digital forensics and incident response (DFIR) process!
Ready to learn Cyber Security? Create your free account today!
TryHackMe provides free online cyber security training to secure jobs & upskill through a fun, interactive learning environment.
Already have an account? Log in

